This post is to list out the procedures of migrating Ubiquiti Unifi to Cisco Meraki wireless, this includes the common configuration of WLAN and SSID, Radius configuration with Microsoft NPS on Server 2022, and troubleshooting tips when you experience problems.
For detailed Microsoft NPS installation and configuration, please check the previous posts:
How to Migrate Microsoft NPS to Server 2019
How to Configure RADIUS Authentication / NPS Server 2022 with Ubiquiti
Environment
- Source: 1x Unifi Cloud Key Gen2, several Ubiquiti Unifi AP AC PRO, and Ubiquiti US-24-250W switches
- Destination: Meraki Cloud Portal, several Cisco Meraki MR46 Access Points and Cisco 9000 Serial switches
- Multiple SSIDs and each SSID is allocated with different VLANs
Source Configuration
1.Each Unifi AP AC PRO is connected at Ubiquiti Switches, Network configuration (VLANs) are defined in Unifi Cloud Controller
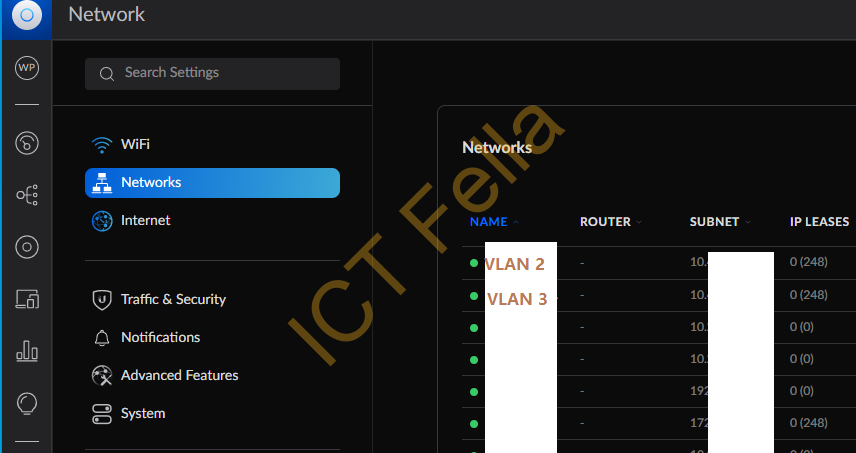
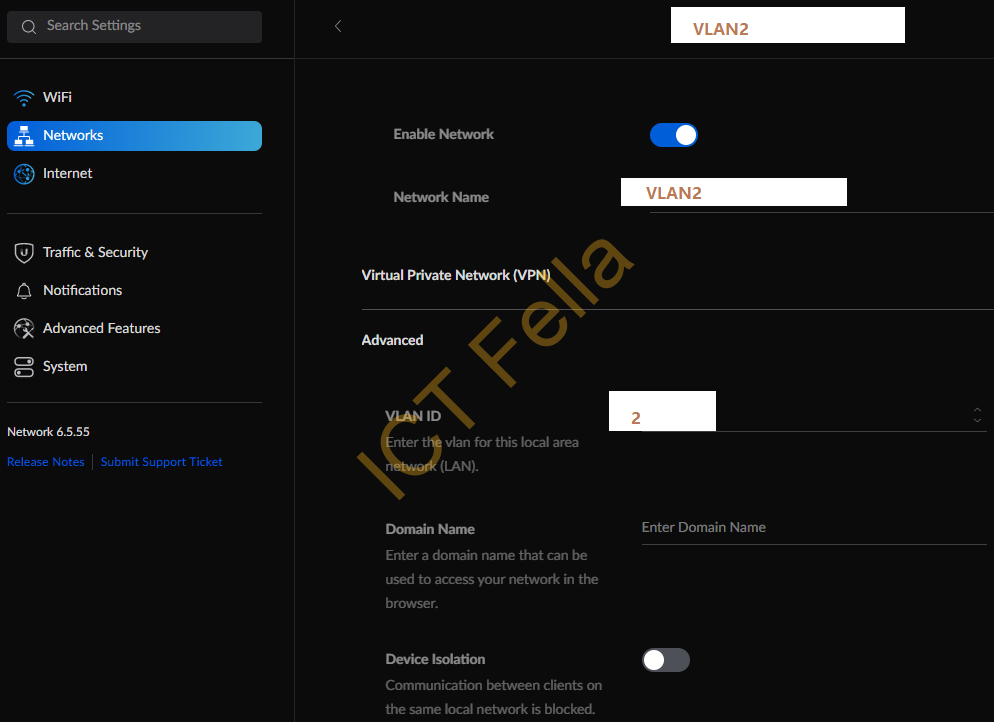
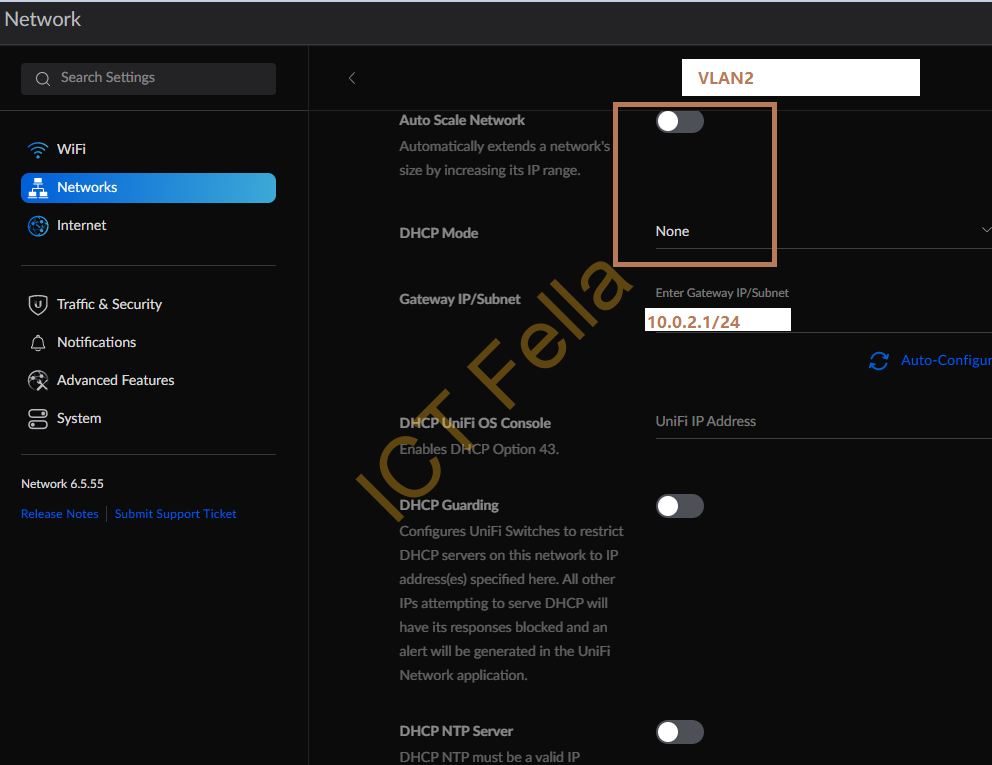
2. Within each “Network” definition, VLAN is defined, DHCP is disabled, and Gateway is defined.
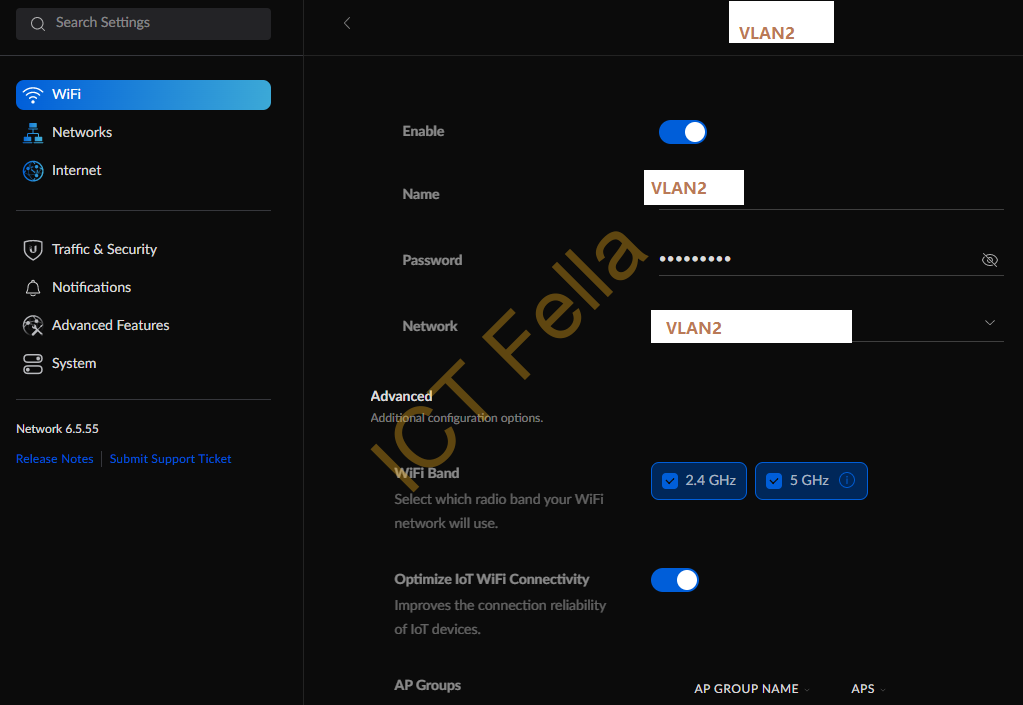
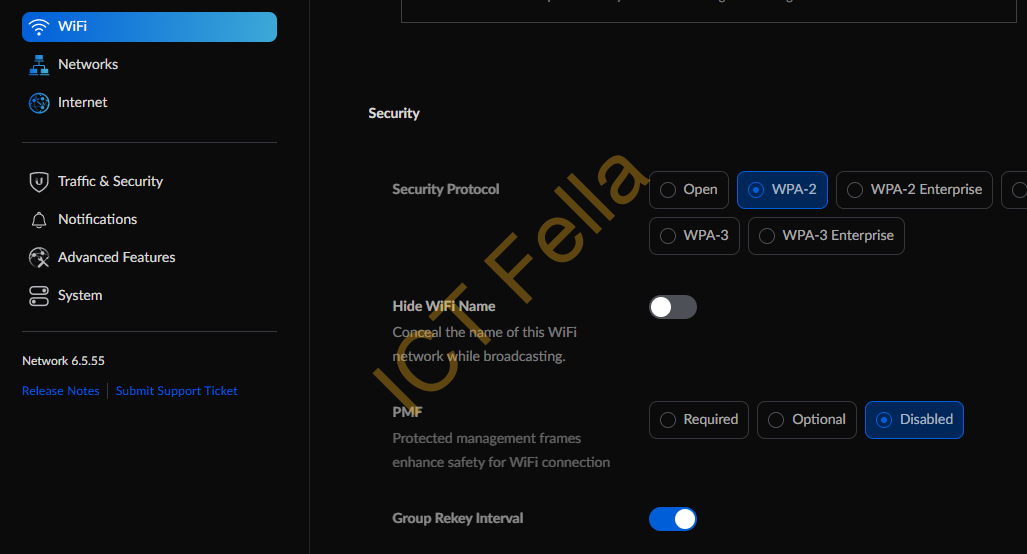
3. WiFi (SSID) configuration that is using either WAP2-Personal authentication:
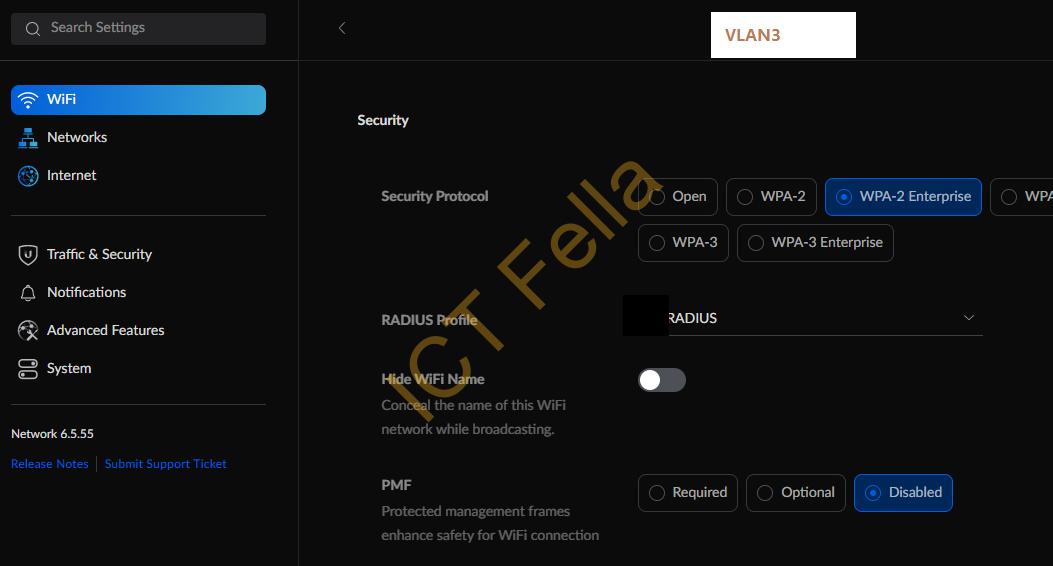
4. (SSID) configuration that is using WAP2-Enterprise authentication:
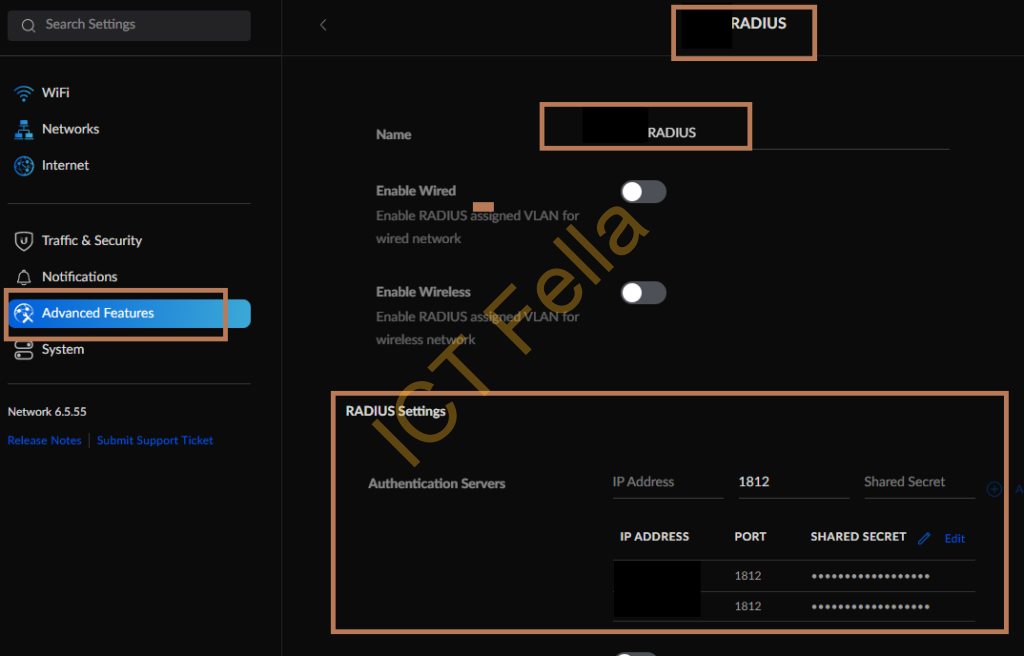
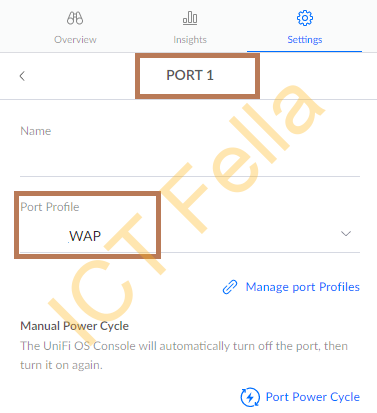
5. Ubiquiti Port configuration for Unifi controllers, port profile configuration, Native VLAN “LAN” means default VLAN1, which is NOT a good practice here.
Destination Configuration
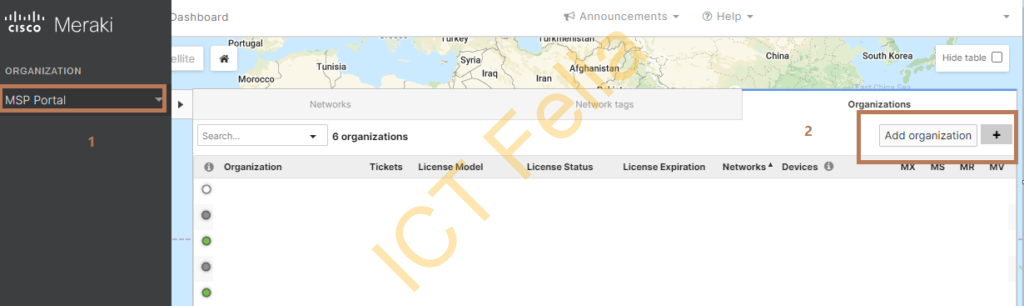
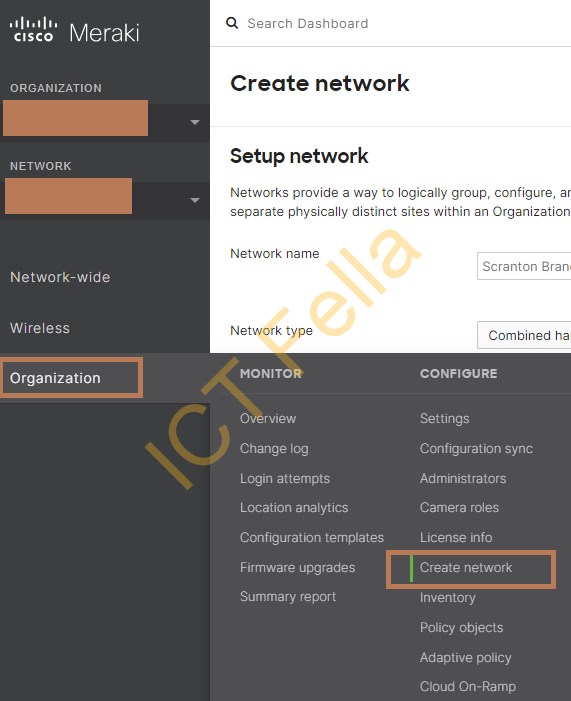
1.Go to the MSP portal, in the list of the organization page, click “Add Organization”, follow the wizard to create the “Network” as well, please note “Network” is more like a location such HQ or Remote Office1, so you can create multiple “Network” to represent a separate set of configurations.
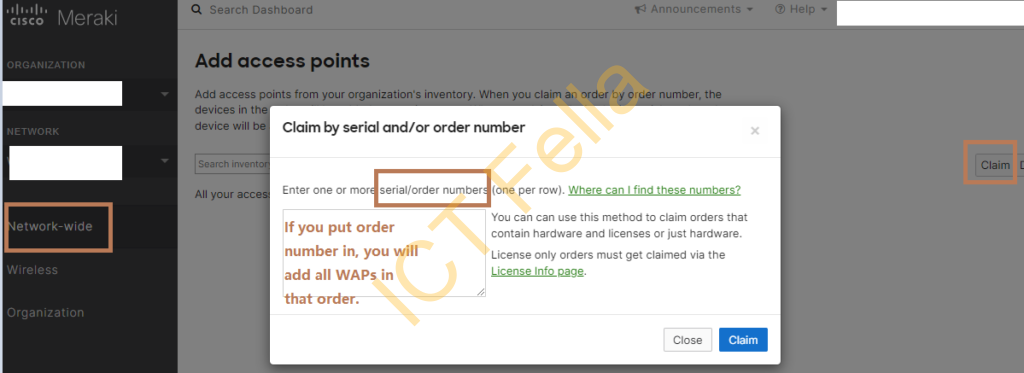
2. Claim the Wireless Access Points
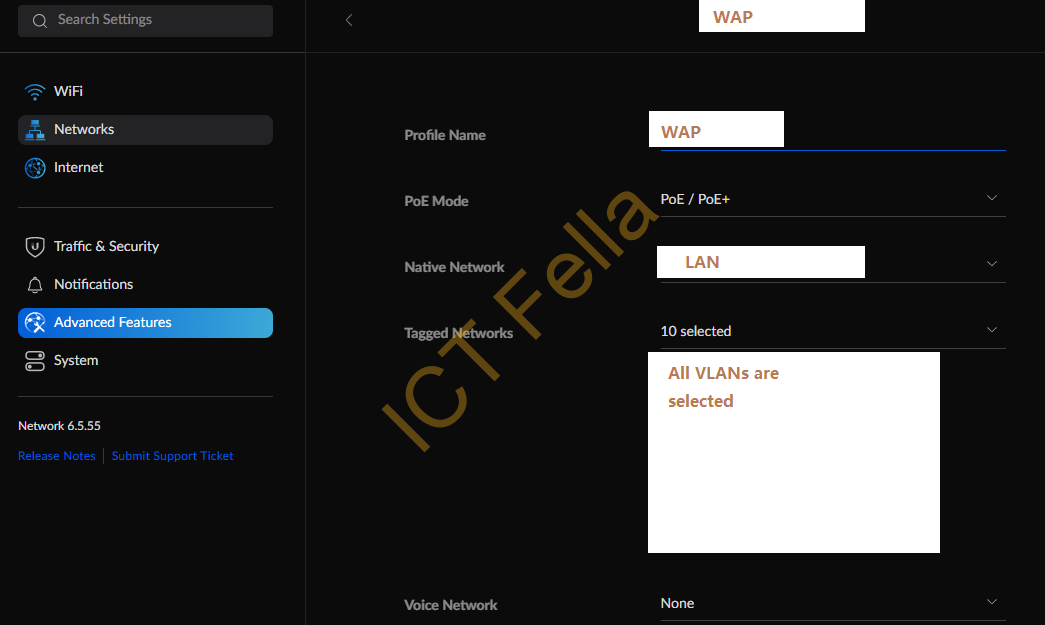
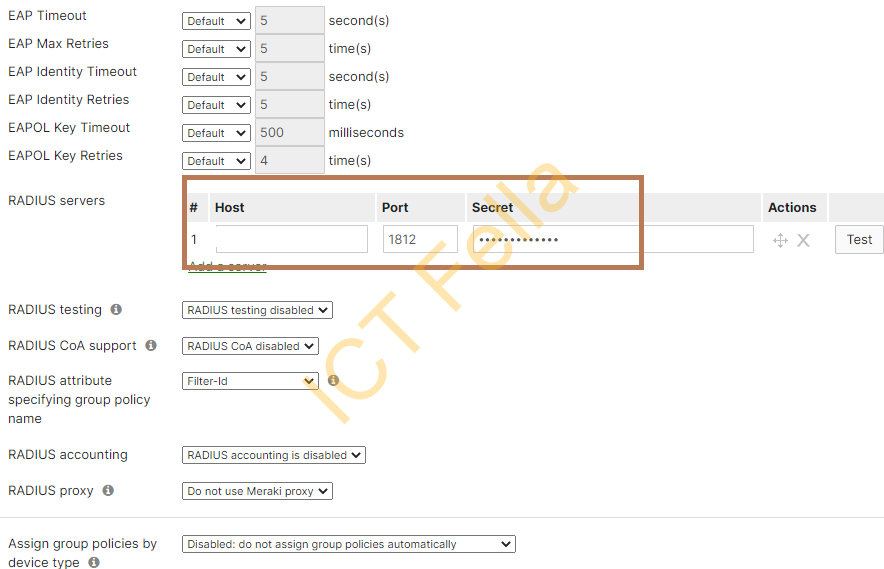
3. WLAN/SSID configuration
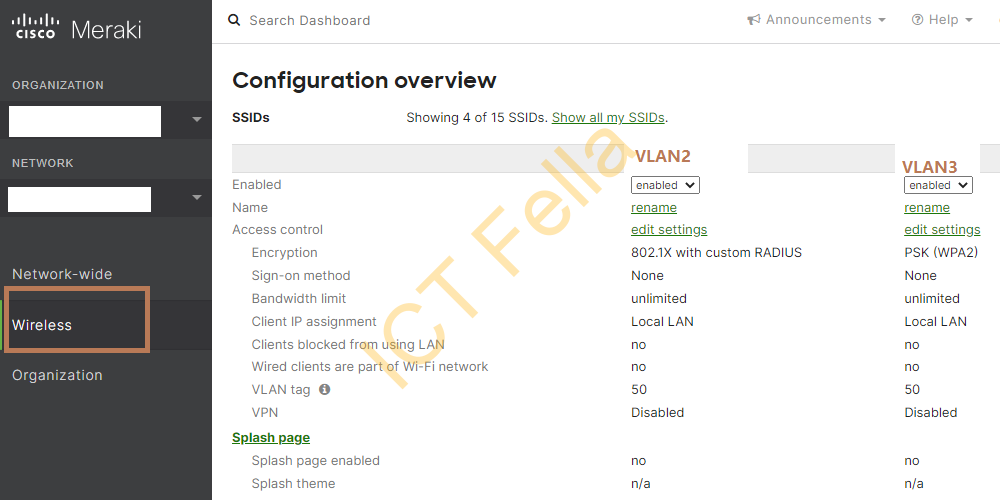
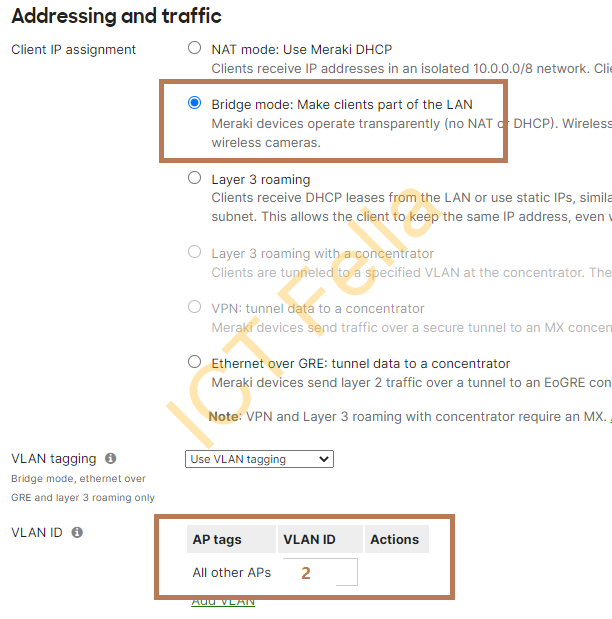
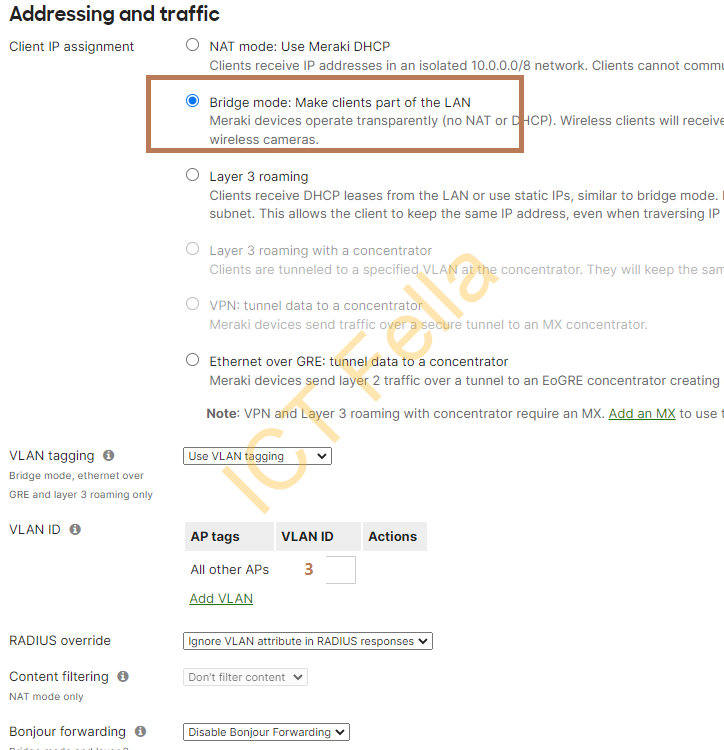
4. SSIDs that use WPA2-Personal authentication, Bridge mode, tagged VLAN2
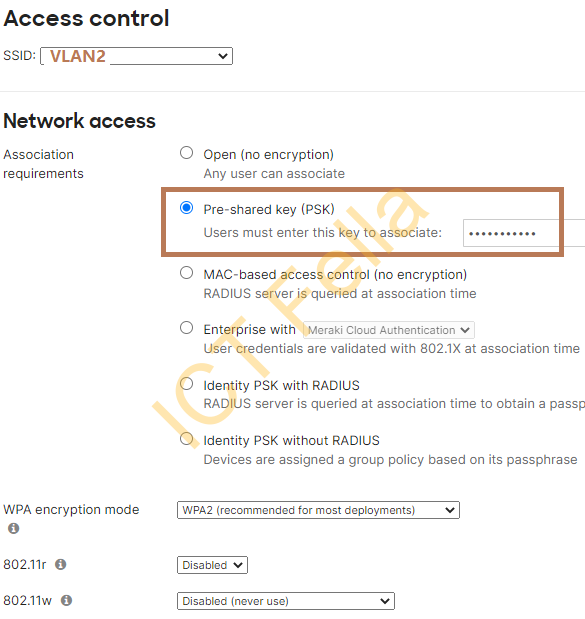
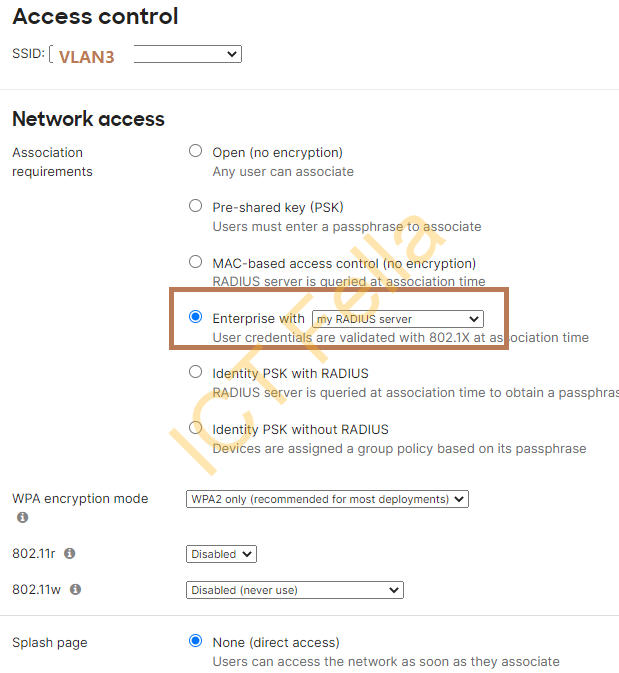
4. SSID that use WPA2-enterprise Authentication, bridge mode, tagged vlan3
5. Cisco Catalyst Switch Configuration
conf t
vlan 2
name VLAN2
vlan3
name VLAN3
interface GigabitEthernet2/0/9
description ***ICTFella_Meraki_WAP***
switchport trunk native vlan X --> Your Meraki WAP management VLAN, please make sure DHCP is working in this VLAN.
switchport mode trunk
interface Vlan2
ip address 10.0.2.1 255.255.255.0
ip helper-address 10.0.0.1
ip helper-address 10.0.0.2
interface Vlan3
ip address 10.0.3.1 255.255.255.0
ip helper-address 10.0.0.1
ip helper-address 10.0.0.2
end
wrCommon issues and causes
Error: Cannot connect to this network
Possible reasons:
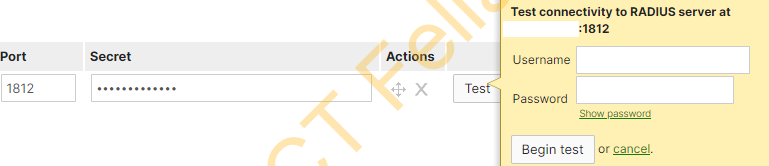
1.Wireless Access Points IPs/subnets are not added to your Microsoft NPS server, you can do a test in the Meraki portal to verify
2. Meraki WAPs are having network connectivity issues to the NPS server, such as routing, firewall ACL
3. Microsoft NPS service is not running well
WiFi connected but no internet
Possible reasons:
1.Check your IP via “ipconfig”, if you are getting a “169.254.x.x” IP, check your DHCP, IP helper-address
2. Missing VLANs in switches, it can be uplink switches along the way
3. VLAN is not allowed on the uplink port to upstream switches
4. VLAN is not allowed Wireless Access Point port
Meraki WAP error: IP address conflict
Possible Reason:
1. DHCP pool overlaps with statically configured devices in that VLAN
Useful links
Configuring RADIUS Authentication with WPA2-Enterprise
