This post is to illustrate the process of configuring the Zscaler GRE tunnel with Cisco ISR for cloud internet security. The main goal of this configuration is to set up the GRE tunnel and send all internet traffic via the tunnel for web filtering, when Tunnel is not available, traffic falls back to the standard internet connection.
Network Topology
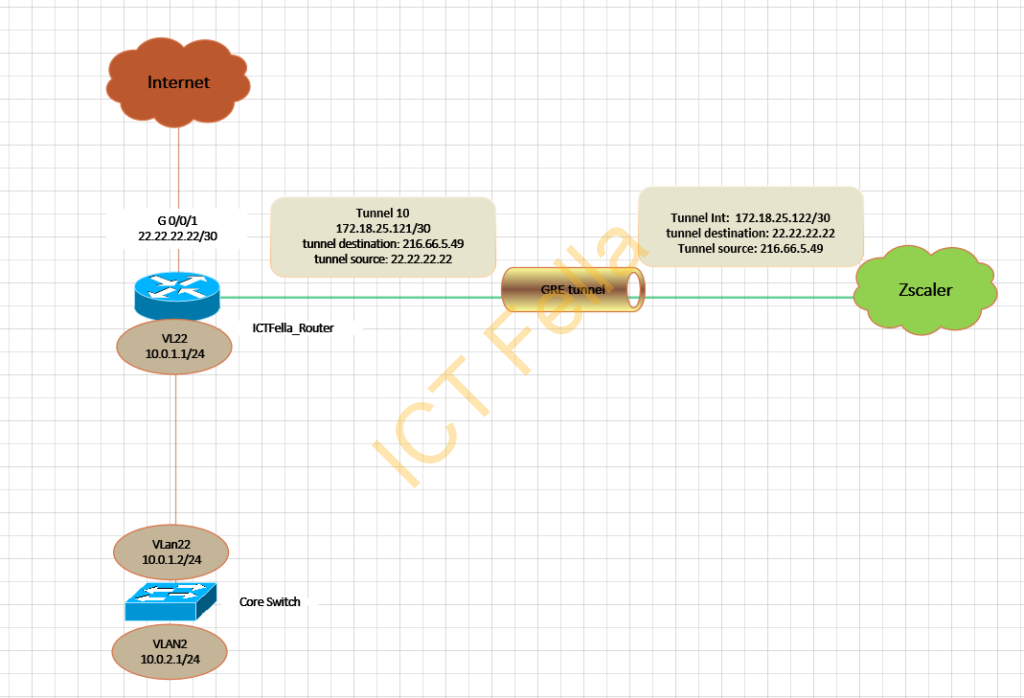
Environment
1. 1x Cisco 4000 Series Integrated Services Router
2. Zscaler cloud security subscription with GRE capability.
3. Static Public IP configured on the router.
Zscaler Admin Portal Configuration
1.Log into Zscaler’s admin portal, logged a ticket to support to pre-configure the GRE tunnel for you on their end, you can give them a simple table like below
| Location | Source Public IP | Primary Destination Public IP | Secondary Destination Public IP | Primary Destination Internal Range | Secondary Destination Internal Range | Physical Location |
| Location A | 22.22.22.22 | 216.66.5.49 | 165.225.226.42 | ? | ? | Your Address A |
| Location B | 33.33.33.33 | 216.66.5.49 | 165.225.226.42 | ? | ? | Your Address B |
2. Once you got the information for the other end, you will be able to “Add Location” from the “Administration” Tab
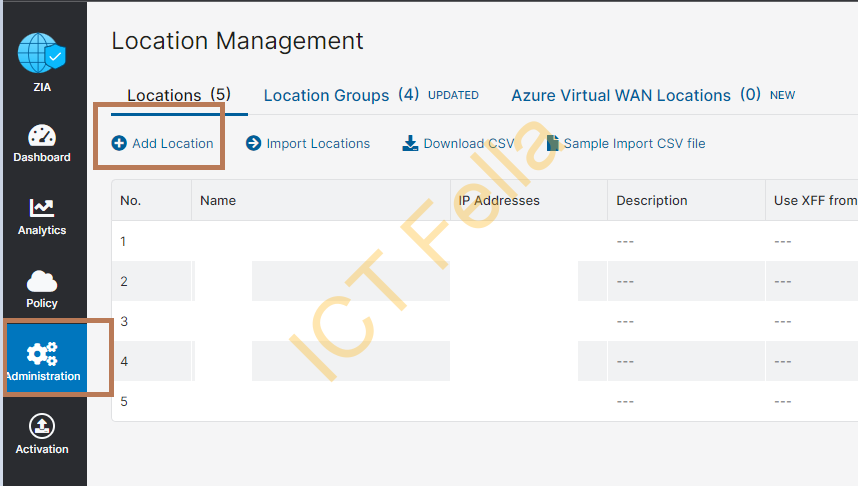
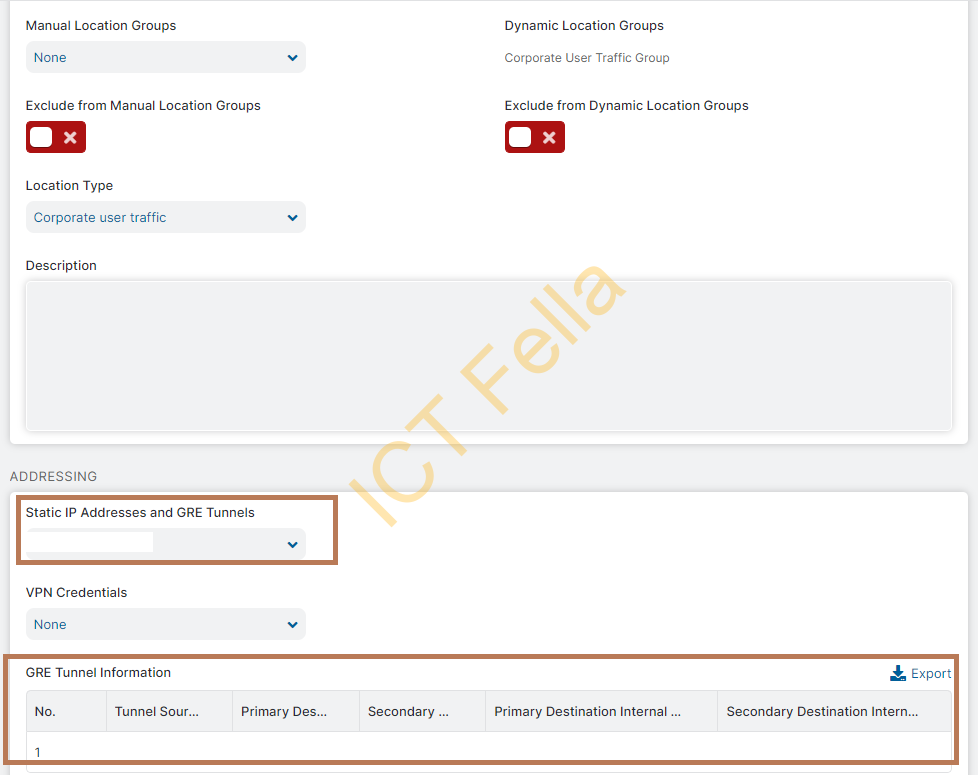
3. you will be able to select your public static IP address and GRE tunnel information
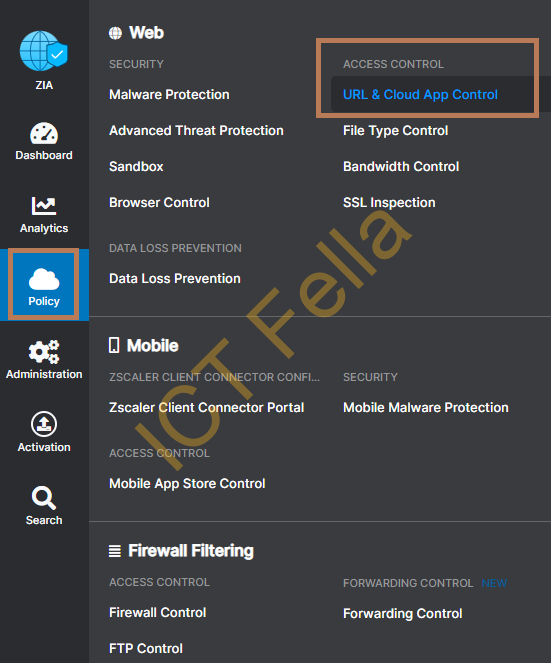
4. You then can create a new URL Filtering Policy using the created location to permit or block traffic based on category or your definition
Cisco ISR configuration
Please be aware we are not using the 2nd tunnel as the failover is using direct internet.
=======Interface Config=============
interface Tunnel10
description *** Zscaler Tunnel***
ip address 172.18.25.121 255.255.255.252
tunnel source 22.22.22.22
tunnel destination 216.66.5.49
interface GigabitEthernet0/0/0.921
description *** to Core SWI ***
encapsulation dot1Q 22
ip address 10.0.1.1 255.255.255.0
ip nat inside
ip policy route-map rm-PBR
interface GigabitEthernet0/0/1
description *** Internet Interface ***
ip address 22.22.22.22 255.255.255.252
ip nat outside
load-interval 30
media-type rj45
negotiation auto=========NAT and Routing Config=============
ip nat inside source route-map rm-NAT interface GigabitEthernet0/0/1 overload
ip route 0.0.0.0 0.0.0.0 22.22.22.21
ip route 8.8.4.4 255.255.255.255 172.18.25.122 name Zscaler-test
ip route 10.0.2.0 255.255.255.0 10.0.1.2 name internal-Subnet========ACL for the Route Map============
ip access-list extended acl-NAT
10 deny ip any 10.0.0.0 0.255.255.255
20 permit ip 10.0.2.0 0.0.0.255 any
ip access-list extended acl-Zscaler
10 deny ip 10.0.2.0 0.0.0.255 host 1.1.1.1
30 deny ip 10.0.2.0 0.0.0.255 10.0.0.0 0.255.255.255
40 deny ip 10.0.2.0 0.0.0.255 172.16.0.0 0.15.255.255
50 deny ip 10.0.2.0 0.0.0.255 192.168.0.0 0.0.255.255
60 permit ip 10.0.2.0 0.0.0.255 any===========IP SLA and Tracking======================
ip sla 20
icmp-echo 8.8.4.4 source-interface Tunnel10
frequency 10
ip sla schedule 20 life forever start-time now
track 20 ip sla 20 reachability
delay down 20 up 20
=====Route Map PBR========
route-map rm-NAT permit 10
match ip address acl-NAT
match interface GigabitEthernet0/0/1
!
route-map rm-PBR permit 20
match ip address acl-Zscaler
set ip next-hop verify-availability 172.18.25.122 1 track 20
!
route-map rm-PBR permit 30Useful links
GRE Configuration Guide for Cisco 881 ISR
https://help.zscaler.com/zia/gre-configuration-example-cisco-881-isr
