Object
This post will list out the step-by-step procedure to migrate the NPS role from server 2016 to server 2019.
Environment
- The source server is Windows Server 2016 standard
- The destination is Windows Server 2019 standard
Install NPS role on the destination server 2019
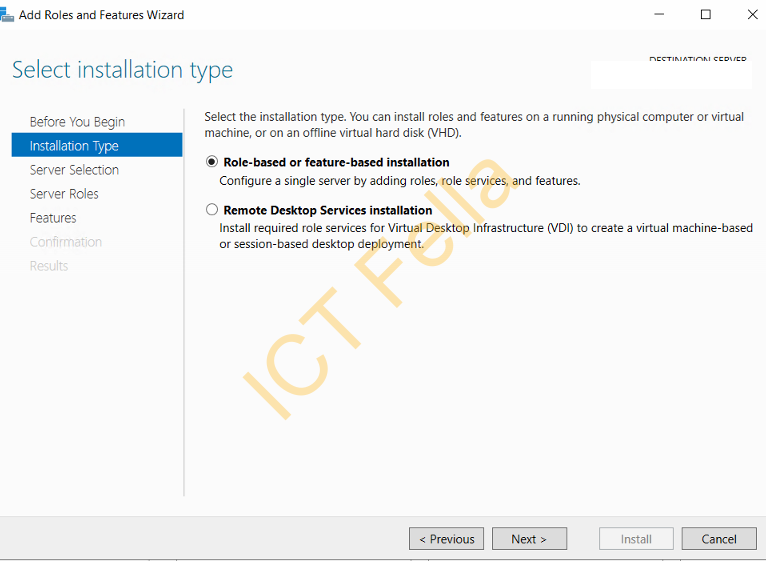
1. Go to Server Manager and click “Add Roles and Features” to start the wizard, then select “Role-based or feature-based Installation”
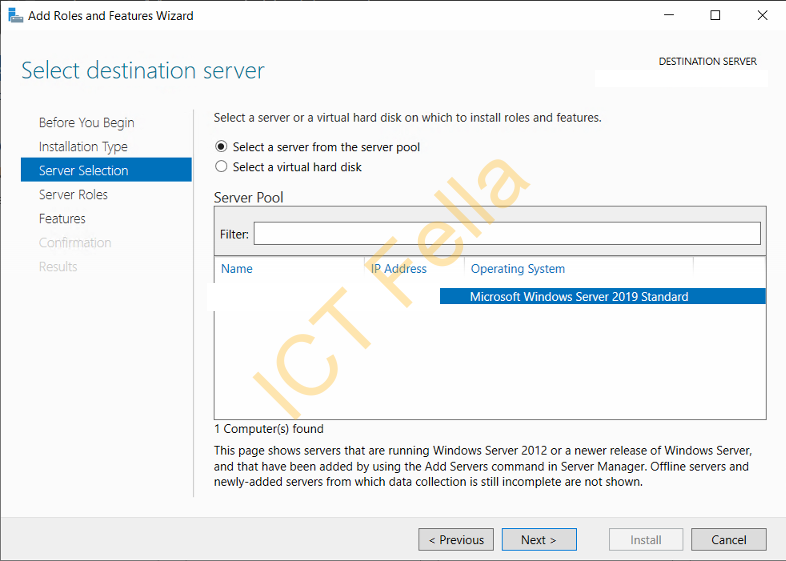
2. Select your server and next
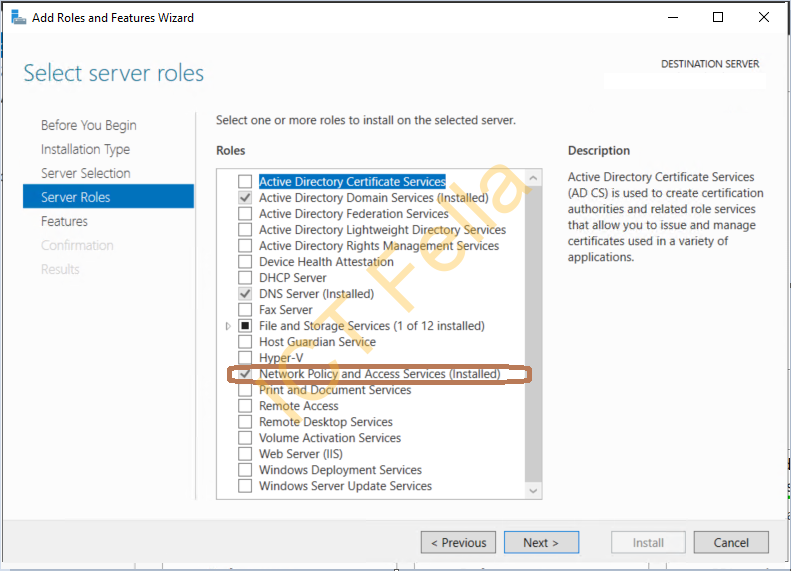
3. Tick “Network Policy and Access Services” then next, next, next until you completed the wizard, please go-ahead to install the “Administrative tools” when asked by the wizard
4. Go to Windows “Administrative Tools” and open “Network Policy Services”
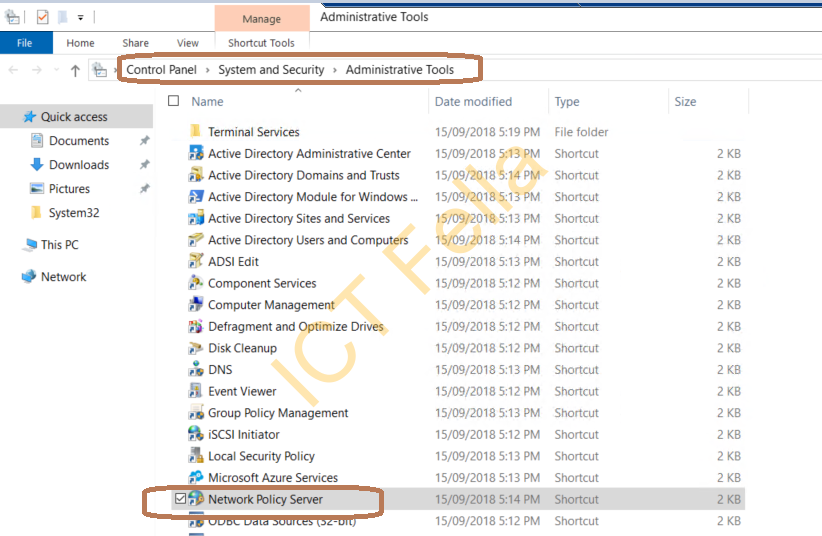
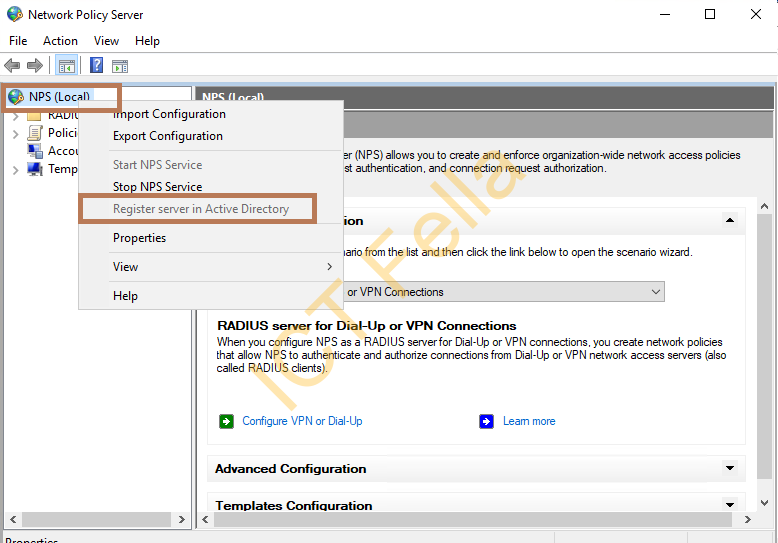
5. Open the “Network Policy Server” window, right-click “NPS (Local)” then select “Register server in Active Directory” and go-ahead for the registration process, you will then see the option is greyed out after registration.
NPS Role Migration
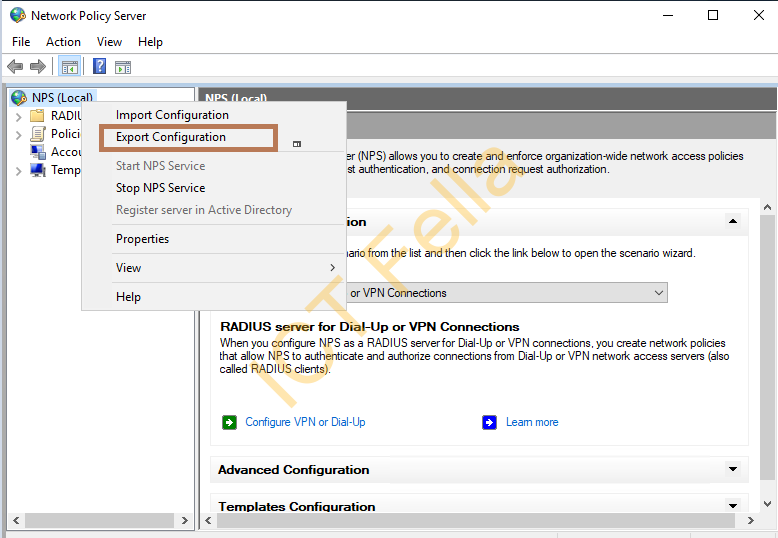
1. on the Source Server 2016, right-click on “NPS (local)” then select “export Configuration”
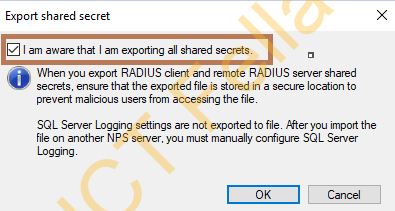
2. In the “Export Shared Secret” warning window, tick the “I am aware that I am exporting all shared secrets” option, then select the location and name for the configuration .xml file
3. Now go to the destination server and import the configuration
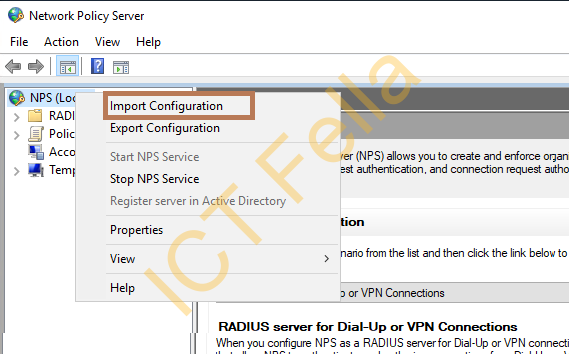
4. After all, you can log into your server/services that using NPS Radius Service, update the IP address to the newly implemented NPS server IP.
5. If you want the “High Availability” of NPS service, repeat the process above and import the configuration onto another server.
Troubleshooting
After the steps, you may find out the NPS is not working, because we are using this server for Wireless Certificate-based authentication, checking the Juniper Mist Cloud portal, gave me the error “Radius Server failed to respond to the request (514).
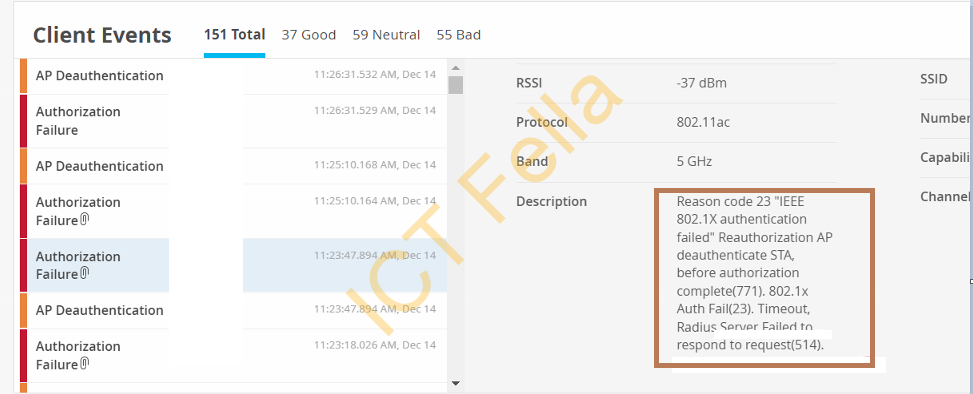
The annoying thing is you can see the client is getting IP address but stuck at the “completing authentication” process, the issue is on the NPS, digging around and found the issue is the Windows Server 2019 bug for IAS
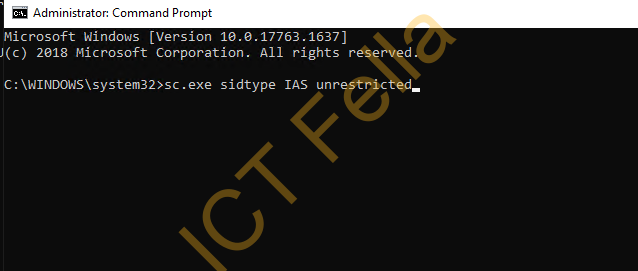
Solution
- Run Windows Comand Prompt as Administrator, and run “sc.exe sidtype IAS unrestricted“