This Post is the last part of Configuring Azure Hub and Spoke – Configure Forced Tunnel so all traffic (paritcularly internet traffic) can be routed via the IPsec tunnel.
Overall Topology
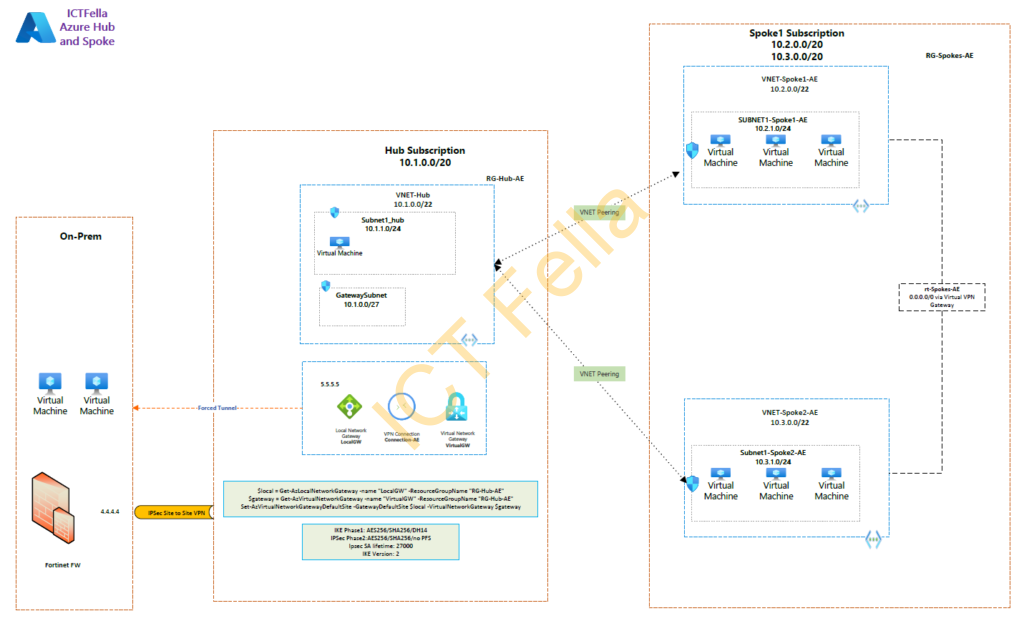
Environment
*On-prem Environment has a pair of Fortinet Fortigate firewalls with a public IP of 4.4.4.4
*Hub and Spoke are on different subscriptions. Note: they can sit within the same subscription or each spoke has its own subscription, the boudary of each location is the Virtual Network (VNET), not subscriptions.
*Virtual Network Gateway (with local gateway and connection in between) are configured with IPsec VPN to provide on-prem network access
*Internet access in Azure is routed over IPsec VPN – Forced Tunnel
* VNET peerings are used to connect the hub and spokes
* We are NOT using “Azure Virtual Network Manager” at this stage because it is still on preview and provided without an SLA by Microsoft.
*Both Intranet and Internet traffic will be routed over the IPsec Tunnel because of company security requirements.
Previous Post – Part 1 and Part 2
Install Azure PowerShell module
Install-Module Az
Connect-AzAccount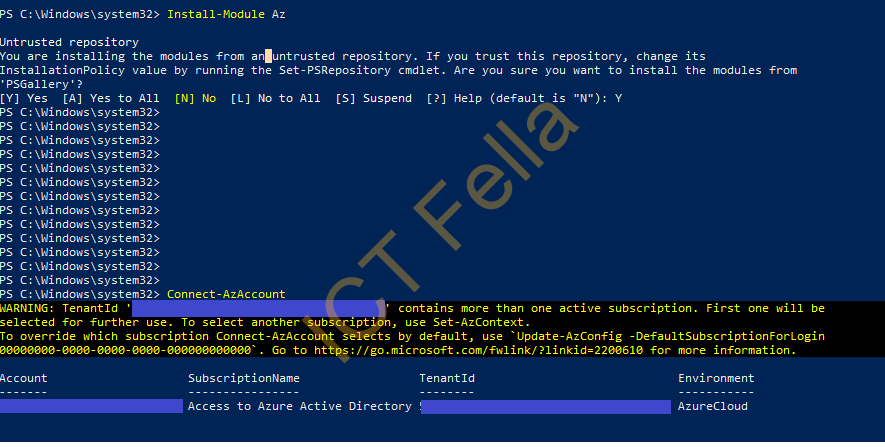
Select the Azure Suscription
In this case, we select the “Hub” suscription as all spoke traffic are routed via it
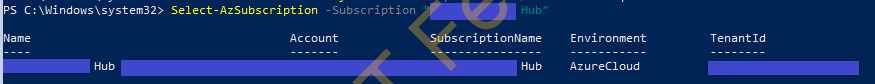
Get-AzSubcription
Select-AzSubscription -Subscription "Hub"

Configure Forced Tunnel on “Hub” Subscription
$local = Get-AzLocalNetworkGateway -name "LocalGW" -ResourceGroupName "RG-Hub-AE"
$gateway = Get-AzVirtualNetworkGateway -name "VirtualGW" -ResourceGroupName "RG-Hub-AE"
Set-AzVirtualNetworkGatewayDefaultSite -GatewayDefaultSite $local -VirtualNetworkGateway $gateway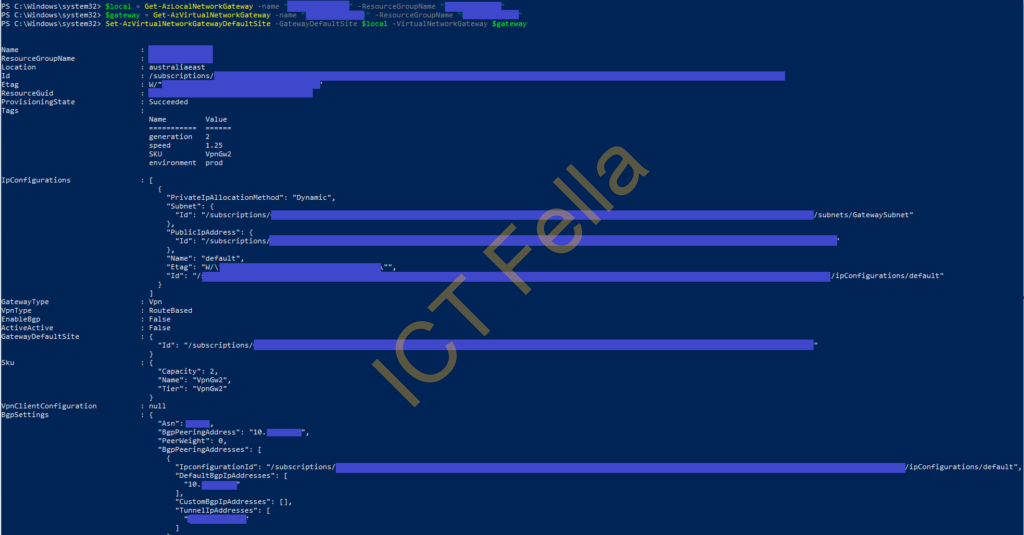
Fortigate Firewall Configuration
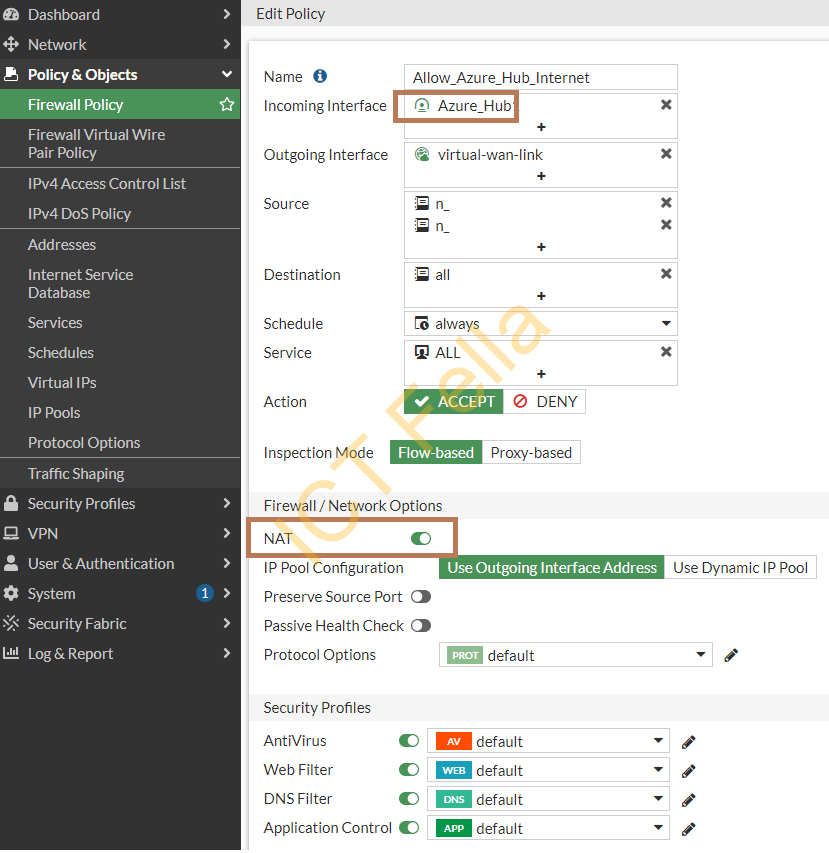
Allow Azure Hub traffic and configure NAT
Useful link
Configure forced tunneling for Site-to-Site connections – Azure VPN Gateway | Microsoft Learn
