This serial of posts is about configuring Azure Hub and Spoke topology, as well as connecting Azure with On-prem environment over IPsec VPN.
Overall Topology
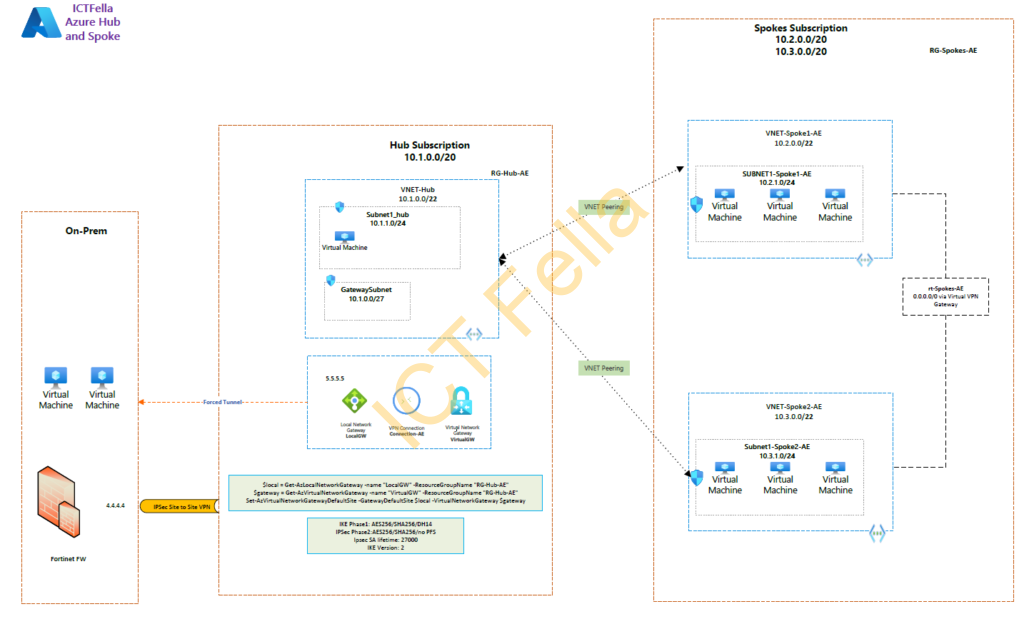
Environment
*On-prem Environment has a pair of Fortinet Fortigate firewalls with a public IP of 4.4.4.4
*Hub and Spoke are on different subscriptions. Note: they can sit within the same subscription, or each spoke has its subscription; the boundary of each location is the Virtual Network (VNET), not subscriptions.
*Virtual Network Gateway (with local gateway and connection in between) are configured with IPsec VPN to provide on-prem network access
*Internet access in Azure is routed over IPsec VPN — Forced Tunnel
* VNET peerings are used to connect the hub and spokes
* We are NOT using “Azure Virtual Network Manager” at this stage because it is still on preview and provided without an SLA by Microsoft.
Deploy the VNET for Hub and Spokes
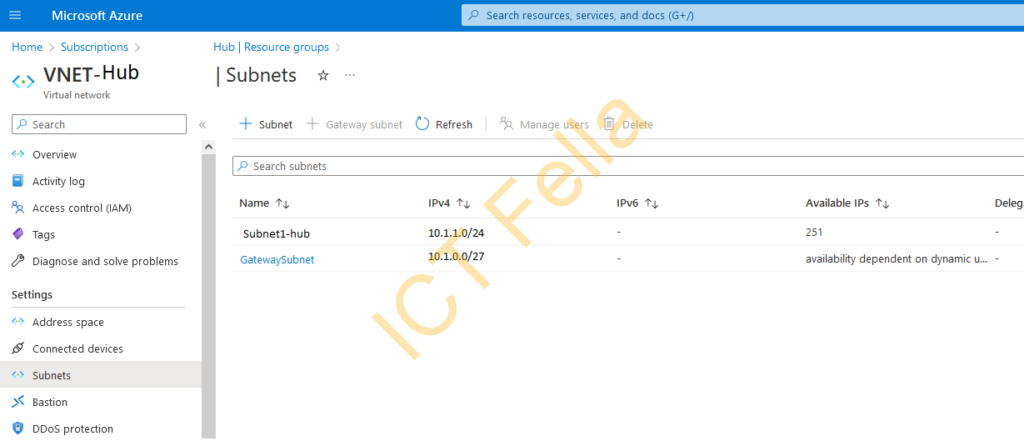
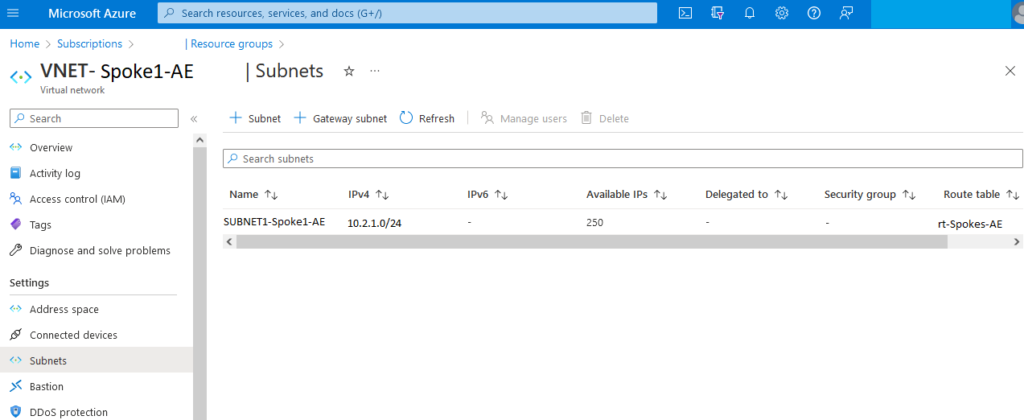
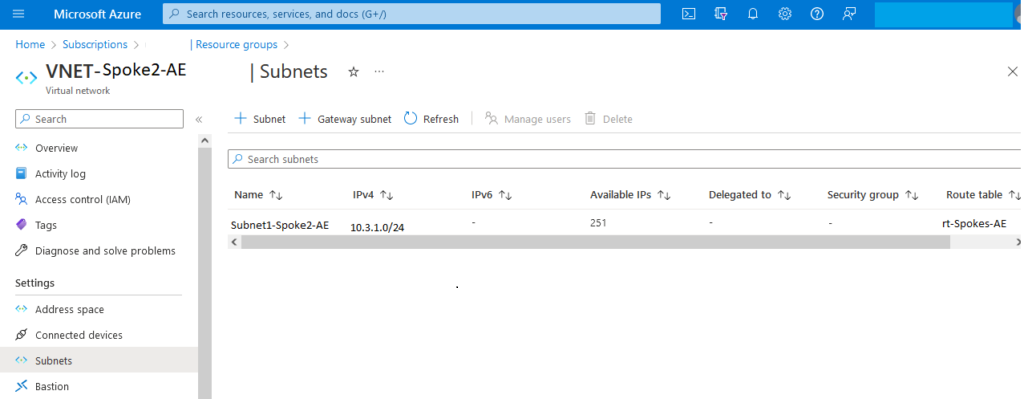
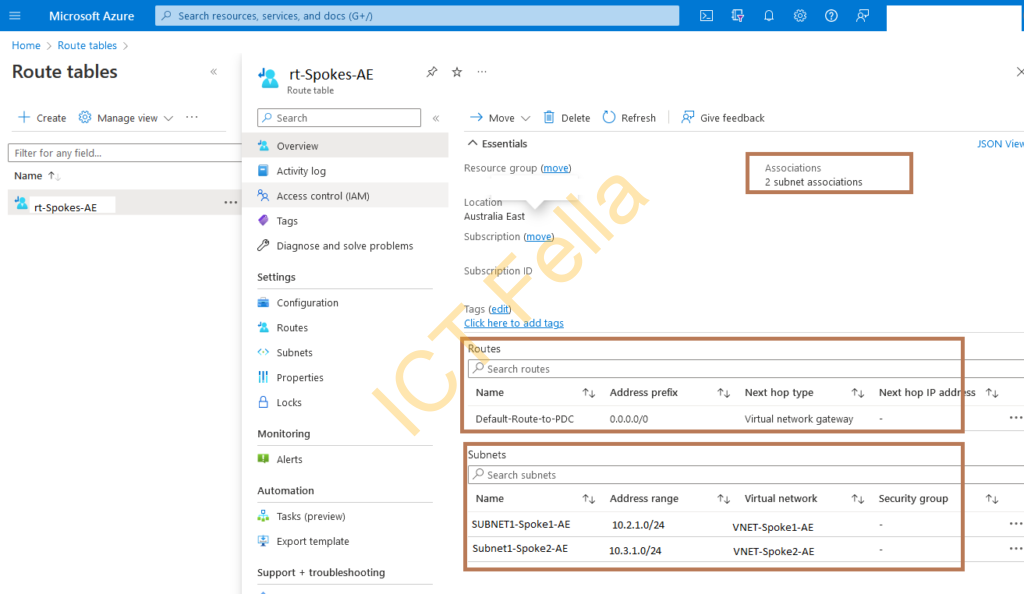
Route Table for two Subnets of two Spokes
A route table called “rt-Spokes-AE” is created and associated with the subnet in each VNET.
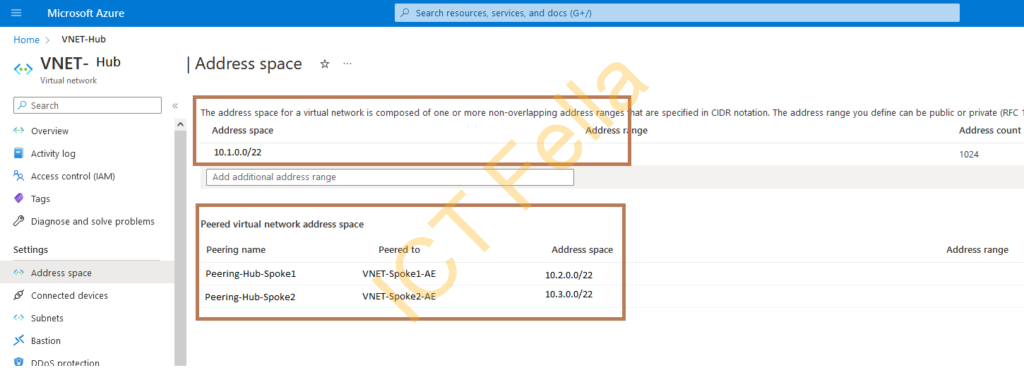
VNET Peering Configuration
In the Peering configuration, please select “Use this virtual network’s gateway or route server” on the Hub side.
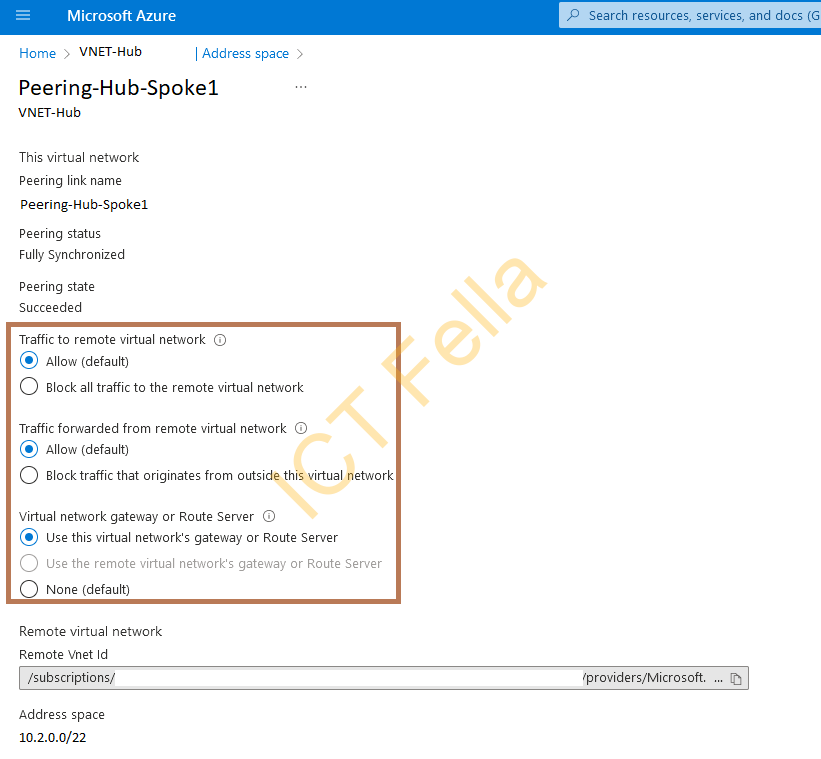
On the Spoke side, you can see “Use the remote virtual network’s gateway or Route Server” is selected automatically

The next post will list out the configurations of IPsec VPN configure between Azure and Fortigate firewall and forced tunnel config so all traffic from Azure will be routed over IPsec VPN and filtered by Fortigate firewall.
