This post is about the configuration of IPsec VPN between Azure and Fortinet Fortigate firewall, as part 2 of the post “How to Configure Azure Hub and Spoke Topology”
How to Configure Azure Hub and Spoke Topology Part 1
Overall Topology

Environment
*On-prem Environment has a pair of Fortinet Fortigate firewalls with a public IP of 4.4.4.4
*Virtual Network Gateway (with local gateway and connection in between) are configured with IPsec VPN to provide on-prem network access
*Internet access in Azure is routed over IPsec VPN — Forced Tunnel
Azure Hub Configuration
Virtual Network Gateway Configuration
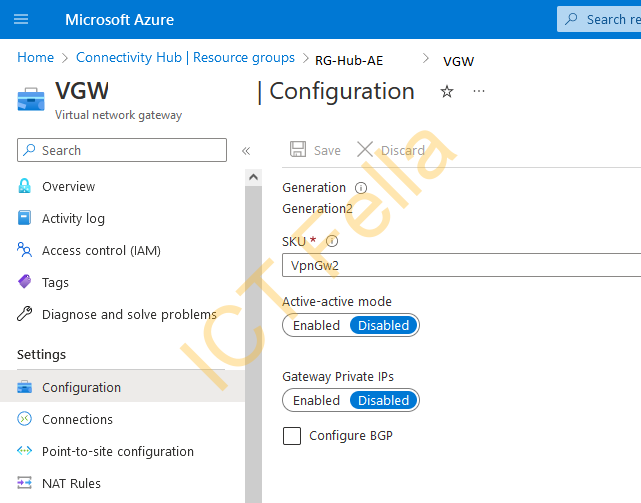
Virtual Network Gateway Connection
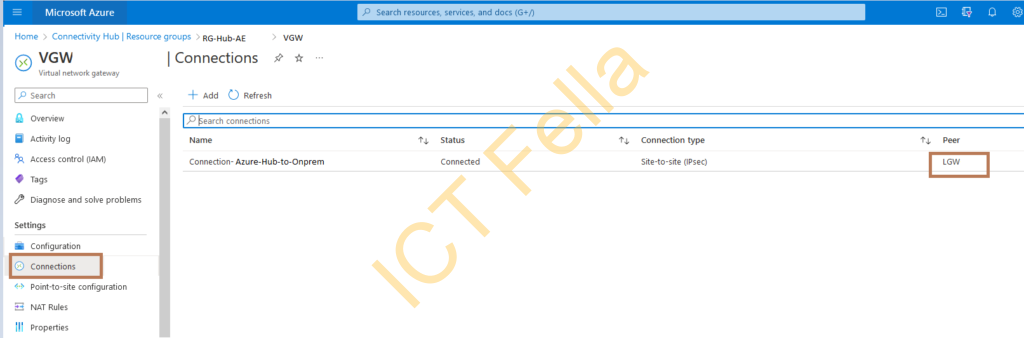
Local Network Gateway Configuration
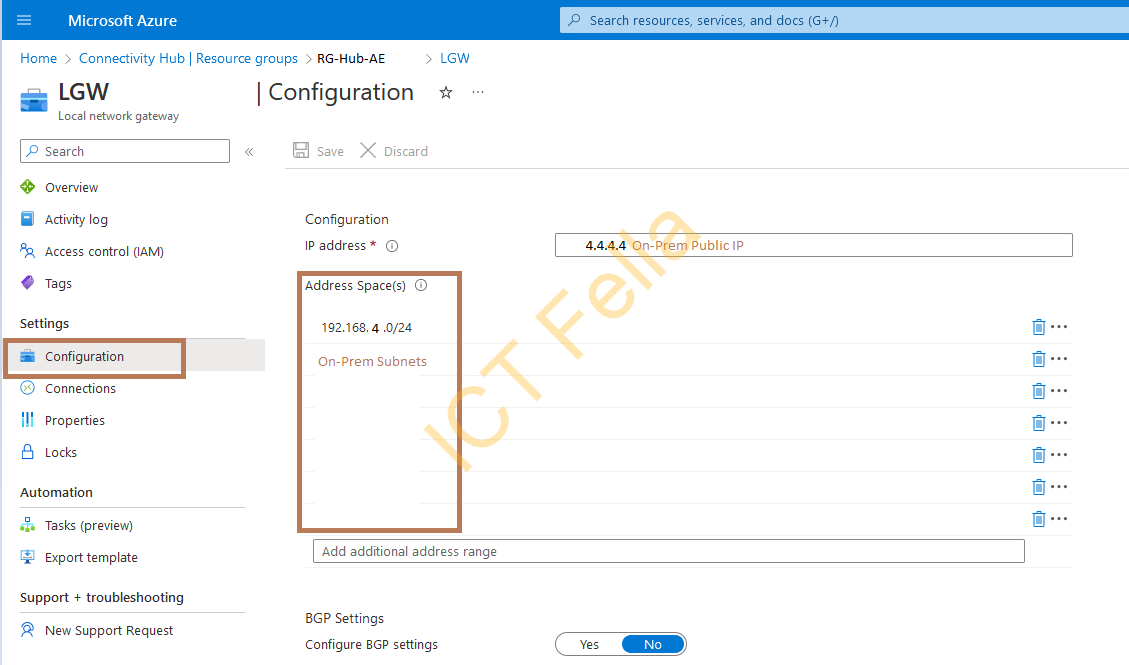
Local Network Gateway Connection
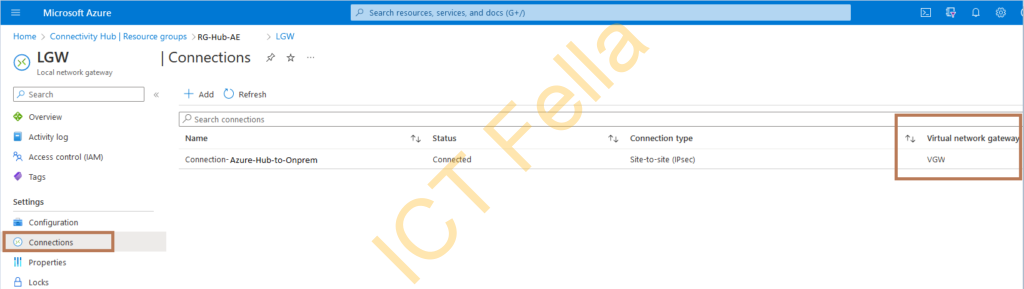
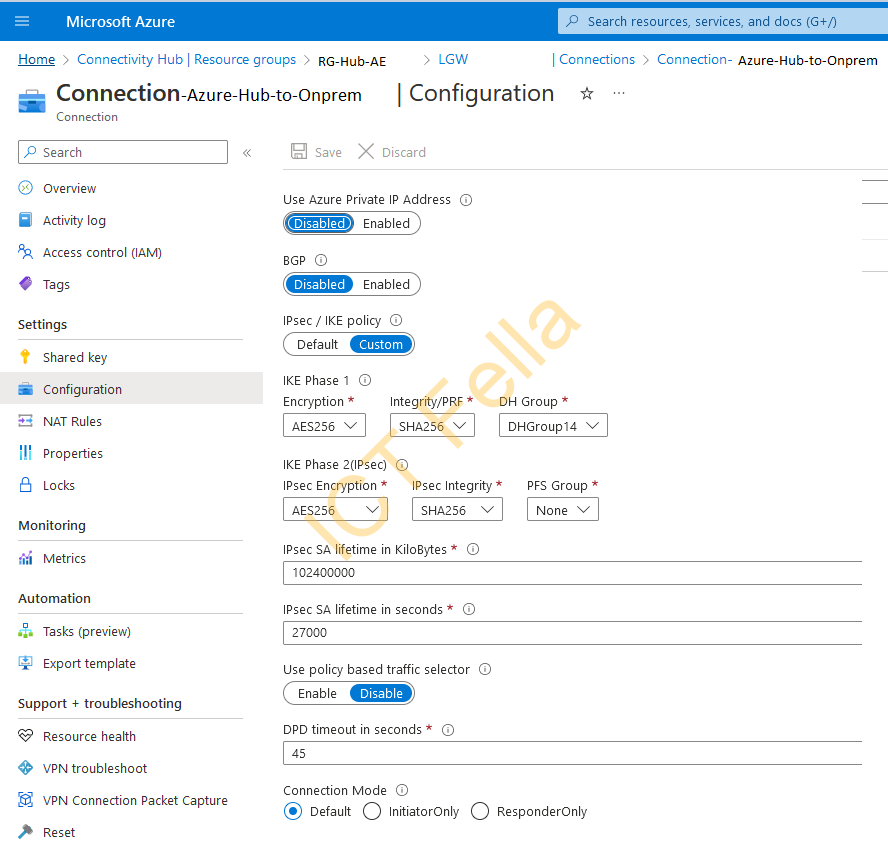
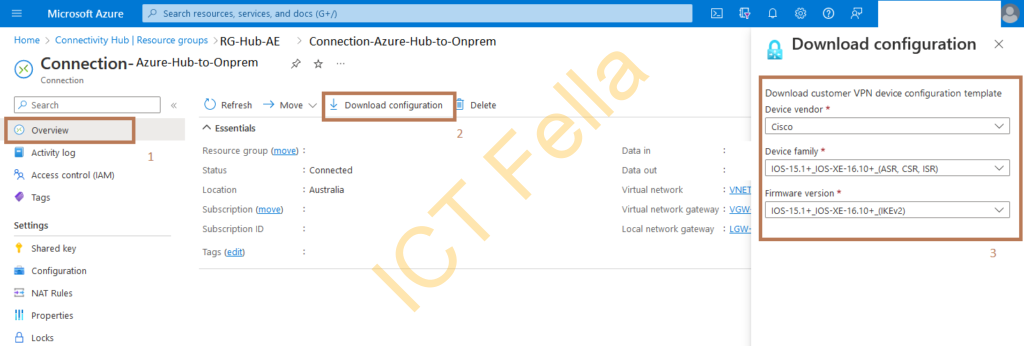
Connection Azure Hub to On-Prem
Feel free to use your preferred IPsec encryption and Integrity settings
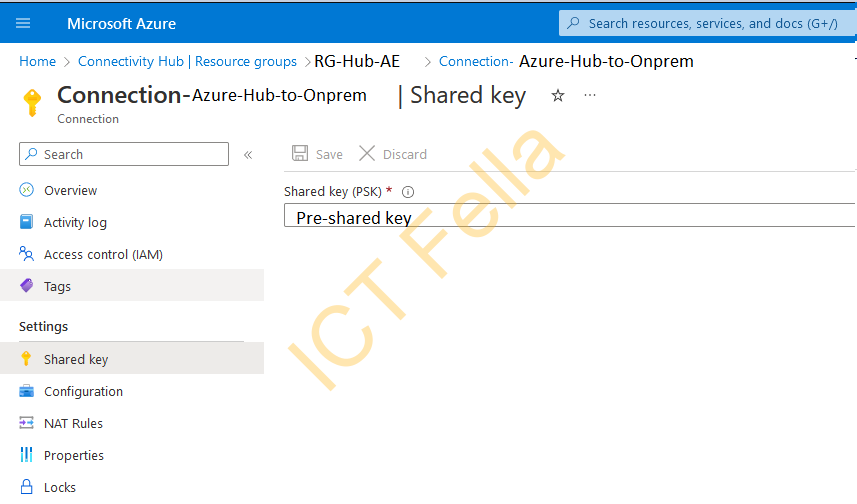
Pre-shared key
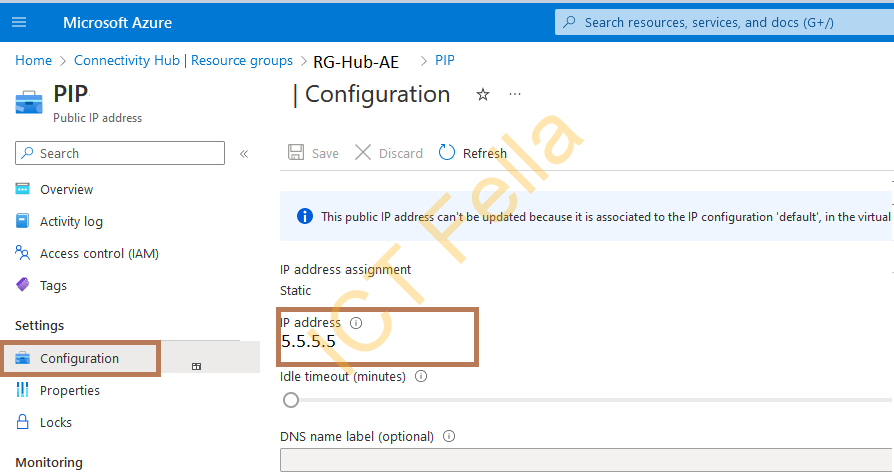
Public IP on Azure Hub
You can download the overall configuration from the “Connection-Azure-Hub-to-onprem”
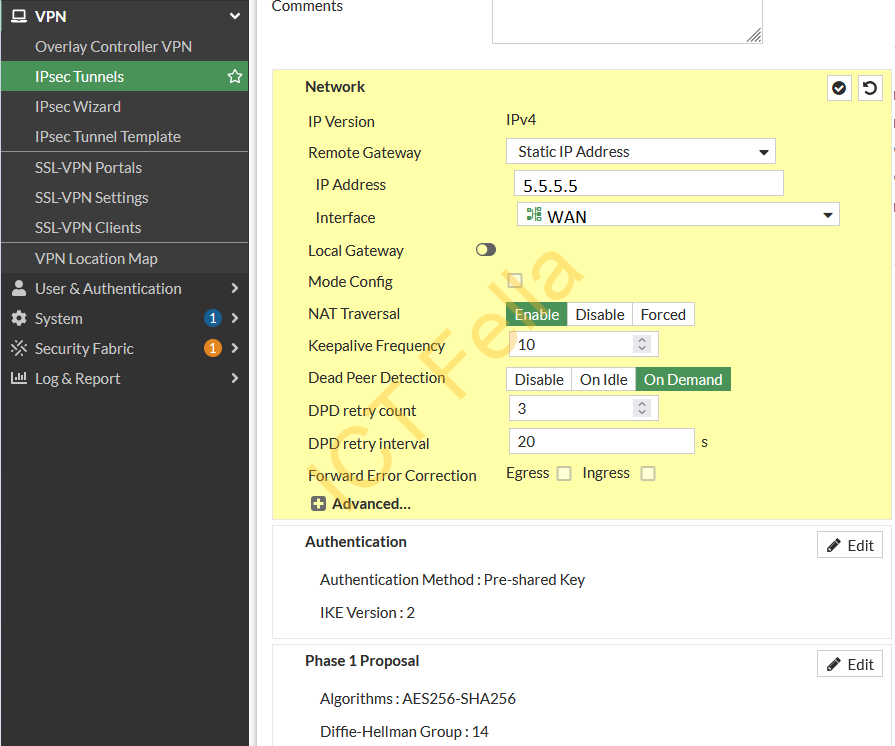
FortiGate Firewall Configurations
Phase 1 Configuration
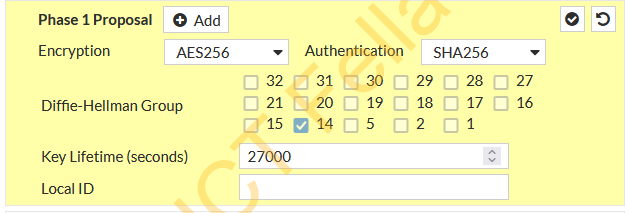
Please make sure your “Key Lifetime” under the “Phase 1 Proposal” is the same as Azure.
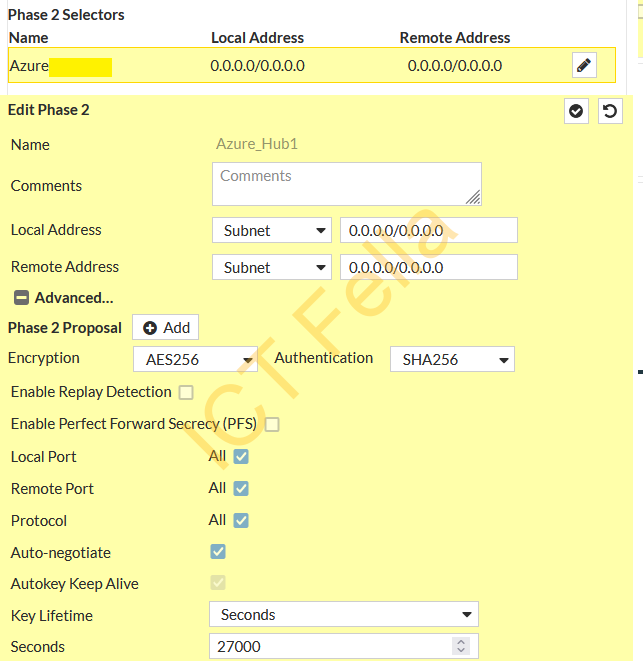
Phase 2 Configuration
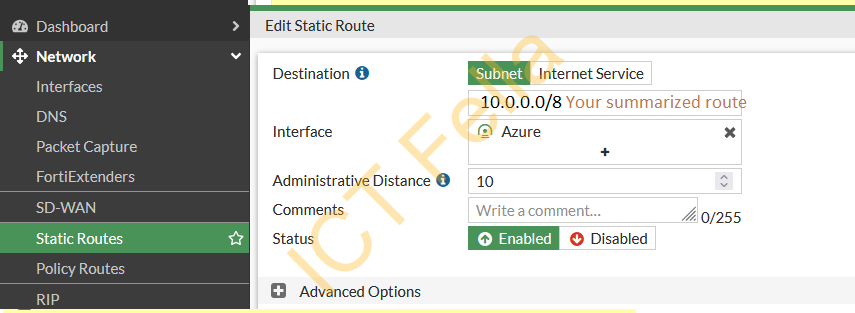
Static Route for Azure Subnets
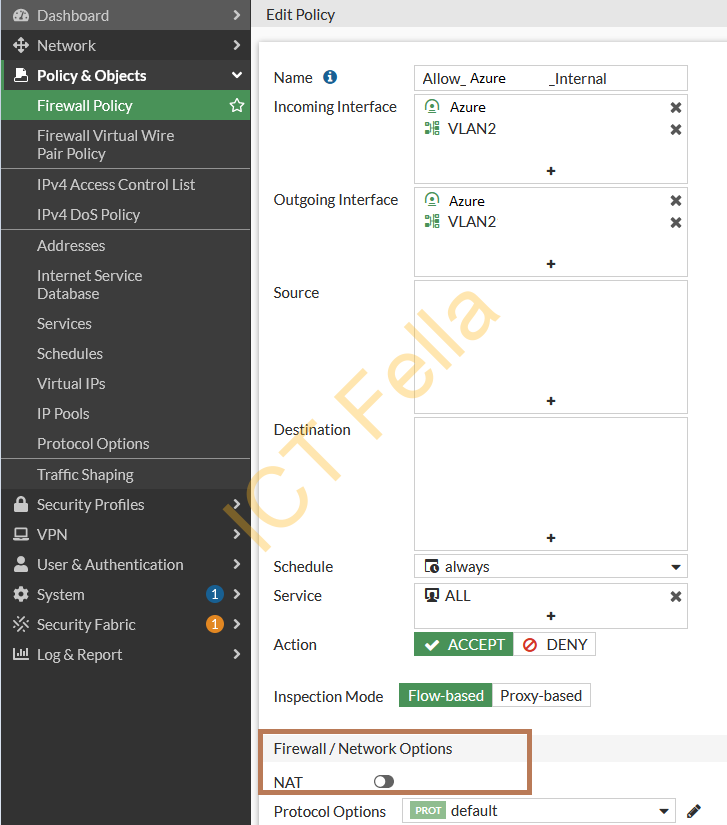
Security Policies
Useful links
https://learn.microsoft.com/en-us/azure/vpn-gateway/vpn-gateway-ipsecikepolicy-rm-powershell
