This post is about using Yubikey with OpenPGP for SSH Key Authentication.
The previous post has talked about how to generate master and subkeys with OpenPGP and copy them into Yubikey
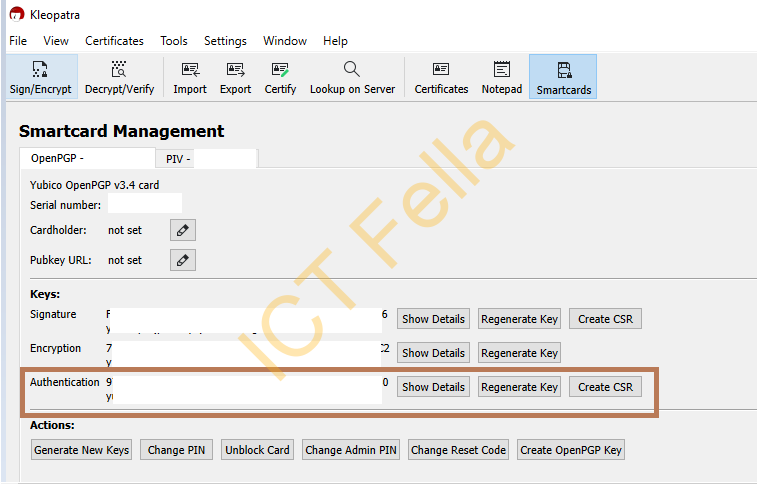
The “Authentication” subkey generated there will be used for SSH Key authentication against a Linux box.
Preparation on GPG4Win
Go to “Kleopatra — Settings — GnuPG System — Private Keys”, and make sure “Enable SSH support” and “Enable Putty Support” is enabled.
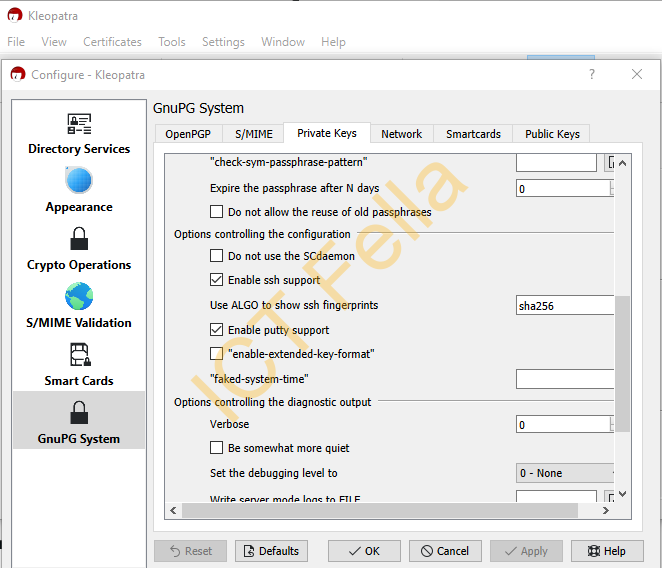
You can also create a file “%appdata%\gnupg\gpg-agent.conf” with below lines in there
enable-ssh-support
enable-putty-supportExport the “Authentication” subkey from Kleopatra
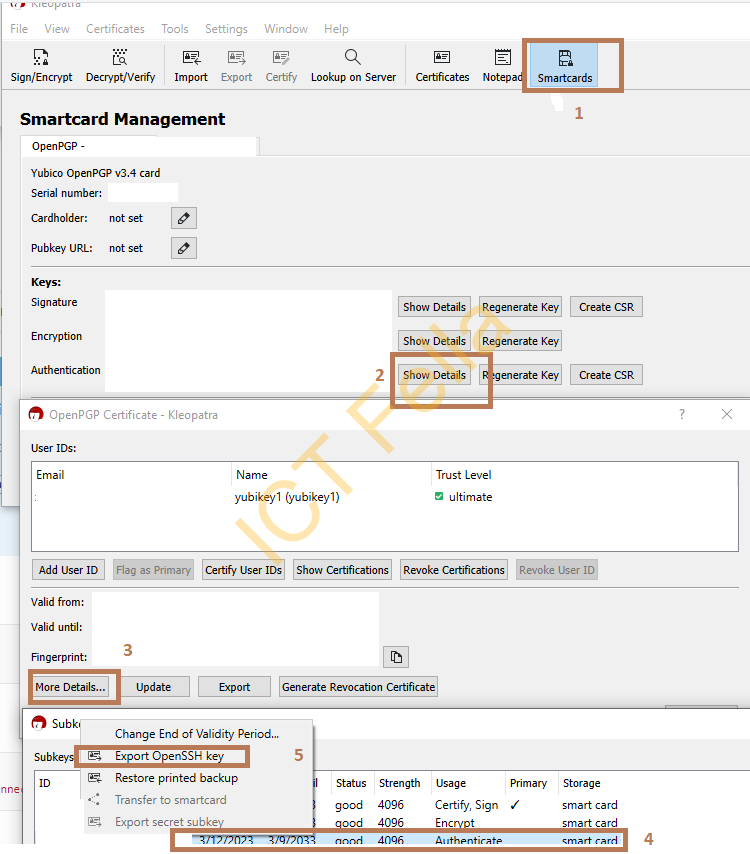
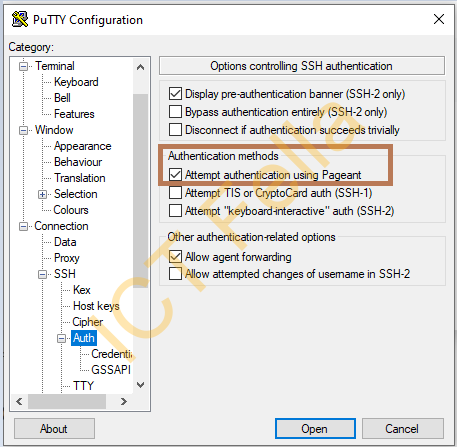
Preparation on Putty
Preparation on your Linux Box
Append your exported OpenSSH key in “authorized_keys” of your Linux box and save
vim ~/.ssh/authorized_keys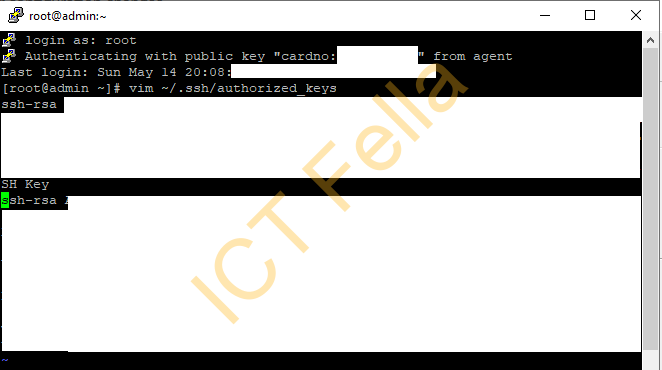
Restart GPG4Win or restart your Windows Computer
GPG4Win is great free software, but it is NOT stable; restartGPG4Win at least, and if Yubikey “smartcard” prompt does not pop up, I would suggest restarting your Windows Computer
gpg-connect-agent killagent /bye
gpg-connect-agent /bye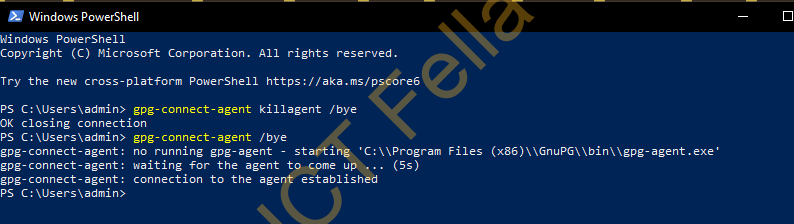
Connect using the Authentication SUbkey on Yubikey
Firstly, start GPG4Win / Kleopatra with Yubikey Connected, and make sure you can see the subkeys.
Then connect using Putty, and enter the Pin of your Yubikey.
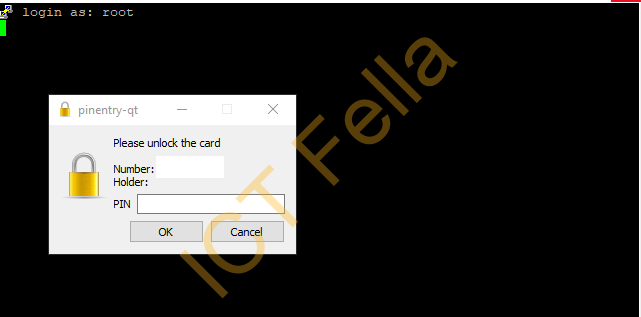
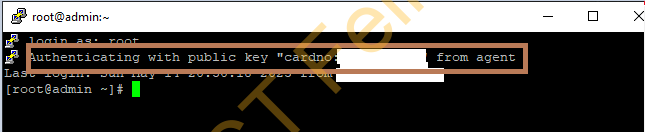
Then you are are in.
Useful links
https://developers.yubico.com/PGP/SSH_authentication/Windows.html
