This post is about configuring Yubikey with GPG — Generate and Import Keys into Yubikey. Yubikey added a “physical layer” of protection on top of GPG.
Environment
GPG keys are generated on the Ubuntu Live CD/USB for security and redundant considerations
2 x Yubikeys, one primary, and one backup.
Generate the Master Key
The first step is to generate the Master key, which is used for Signing and Certifying, shortly “SC”, you can see an “Encryption” sub-key is also generated, shortly “E”
ubuntu@ubuntu:~/Desktop$ gpg --expert --full-gen-key
gpg (GnuPG) 2.2.27; Copyright (C) 2021 Free Software Foundation, Inc.
This is free software: you are free to change and redistribute it.
There is NO WARRANTY, to the extent permitted by law.
Please select what kind of key you want:
(1) RSA and RSA (default)
(2) DSA and Elgamal
(3) DSA (sign only)
(4) RSA (sign only)
(7) DSA (set your own capabilities)
(8) RSA (set your own capabilities)
(9) ECC and ECC
(10) ECC (sign only)
(11) ECC (set your own capabilities)
(13) Existing key
(14) Existing key from card
Your selection? 1
RSA keys may be between 1024 and 4096 bits long.
What keysize do you want? (3072) 4096
Requested keysize is 4096 bits
RSA keys may be between 1024 and 4096 bits long.
What keysize do you want for the subkey? (3072) 4096
Requested keysize is 4096 bits
Please specify how long the key should be valid.
0 = key does not expire
<n> = key expires in n days
<n>w = key expires in n weeks
<n>m = key expires in n months
<n>y = key expires in n years
Key is valid for? (0) 10y
Key expires at Wed 09 Mar 2033 05:33:13 AM UTC
Is this correct? (y/N) y
GnuPG needs to construct a user ID to identify your key.
Real name: Yubikey1
Email address: [email protected]
Comment: Yubikey1
You selected this USER-ID:
"Yubikey1 (Yubikey1) <[email protected]>"
Change (N)ame, (C)omment, (E)mail or (O)kay/(Q)uit? O
We need to generate a lot of random bytes. It is a good idea to perform
some other action (type on the keyboard, move the mouse, utilize the
disks) during the prime generation; this gives the random number
generator a better chance to gain enough entropy.
We need to generate a lot of random bytes. It is a good idea to perform
some other action (type on the keyboard, move the mouse, utilize the
disks) during the prime generation; this gives the random number
generator a better chance to gain enough entropy.
gpg: /home/ubuntu/.gnupg/trustdb.gpg: trustdb created
gpg: key Dxxxxxxxxxxxxxxxx75 marked as ultimately trusted
gpg: directory '/home/ubuntu/.gnupg/openpgp-revocs.d' created
gpg: revocation certificate stored as '/home/ubuntu/.gnupg/openpgp-revocs.d/8xxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxx75.rev'
public and secret key created and signed.
pub rsa4096 2023-03-12 [SC] [expires: 2033-03-09]
85xxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxx75
uid Yubikey1 (Yubikey1) <[email protected]>
sub rsa4096 2023-03-12 [E] [expires: 2033-03-09]
ubuntu@ubuntu:~/Desktop$ gpg --list-secret-keys
gpg: checking the trustdb
gpg: marginals needed: 3 completes needed: 1 trust model: pgp
gpg: depth: 0 valid: 1 signed: 0 trust: 0-, 0q, 0n, 0m, 0f, 1u
gpg: next trustdb check due at 2033-03-09
/home/ubuntu/.gnupg/pubring.kbx
-------------------------------
sec rsa4096 2023-03-12 [SC] [expires: 2033-03-09]
85xxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxx75
uid [ultimate] Yubikey1 (Yubikey1) <[email protected]>
ssb rsa4096 2023-03-12 [E] [expires: 2033-03-09]Generate an “Authentication use” only sub-key
It can be used for SSH login. This is NOT needed if you only use GPG for file/email encryption and decryption.
After this session, we will add another subkey that is “Authenticate” only, shortly “A”
ubuntu@ubuntu:~/Desktop$ gpg --expert --edit-key [email protected]
gpg (GnuPG) 2.2.27; Copyright (C) 2021 Free Software Foundation, Inc.
This is free software: you are free to change and redistribute it.
There is NO WARRANTY, to the extent permitted by law.
Secret key is available.
sec rsa4096/Dxxxxxxxxxxxxxxxxxxxxxxxxxx75
created: 2023-03-12 expires: 2033-03-09 usage: SC
trust: ultimate validity: ultimate
ssb rsa4096/Dccccccccccccxxxxxxxxxxx3F
created: 2023-03-12 expires: 2033-03-09 usage: E
[ultimate] (1). Yubikey1 (Yubikey1) <[email protected]>
gpg> addkey
Please select what kind of key you want:
(3) DSA (sign only)
(4) RSA (sign only)
(5) Elgamal (encrypt only)
(6) RSA (encrypt only)
(7) DSA (set your own capabilities)
(8) RSA (set your own capabilities)
(10) ECC (sign only)
(11) ECC (set your own capabilities)
(12) ECC (encrypt only)
(13) Existing key
(14) Existing key from card
Your selection? 8
Possible actions for a RSA key: Sign Encrypt Authenticate
Current allowed actions: Sign Encrypt (default actions)
(S) Toggle the sign capability
(E) Toggle the encrypt capability
(A) Toggle the authenticate capability
(Q) Finished
Your selection? s
Possible actions for a RSA key: Sign Encrypt Authenticate
Current allowed actions: Encrypt (now Sign is deslected)
(S) Toggle the sign capability
(E) Toggle the encrypt capability
(A) Toggle the authenticate capability
(Q) Finished
Your selection? e
Possible actions for a RSA key: Sign Encrypt Authenticate
Current allowed actions: (now nothing :)
(S) Toggle the sign capability
(E) Toggle the encrypt capability
(A) Toggle the authenticate capability
(Q) Finished
Your selection? a
Possible actions for a RSA key: Sign Encrypt Authenticate
Current allowed actions: Authenticate (now only Authenticate is selected)
(S) Toggle the sign capability
(E) Toggle the encrypt capability
(A) Toggle the authenticate capability
(Q) Finished
Your selection? q
RSA keys may be between 1024 and 4096 bits long.
What keysize do you want? (3072) 4096
Requested keysize is 4096 bits
Please specify how long the key should be valid.
0 = key does not expire
<n> = key expires in n days
<n>w = key expires in n weeks
<n>m = key expires in n months
<n>y = key expires in n years
Key is valid for? (0) 10y
Key expires at Wed 09 Mar 2033 05:48:29 AM UTC
Is this correct? (y/N) y
Really create? (y/N) y
We need to generate a lot of random bytes. It is a good idea to perform
some other action (type on the keyboard, move the mouse, utilize the
disks) during the prime generation; this gives the random number
generator a better chance to gain enough entropy.
sec rsa4096/Dxxxxxxxxxxxxxxxxxxxx75
created: 2023-03-12 expires: 2033-03-09 usage: SC
trust: ultimate validity: ultimate
ssb rsa4096/DxxxxxxxxxxxxxxxxxxxxxxxxxxF
created: 2023-03-12 expires: 2033-03-09 usage: E
ssb rsa4096/Bxxxxxxxxxxxxxxxxxxxxx9C
created: 2023-03-12 expires: 2033-03-09 usage: A
[ultimate] (1). Yubikey1 (Yubikey1) <[email protected]
gpg> quit
Save changes? (y/N) y (Remember to save the config)
ubuntu@ubuntu:~/Desktop$
Export the keys out
The below steps are to back up your keys in case you lost your Yubikey. Please keep your master key and subkey offline for security considerations. Also, we will move those keys (except the public key) into yubikey in the next step.
ubuntu@ubuntu:~/Desktop$ gpg –armor –export-secret-keys [email protected] > master.key
ubuntu@ubuntu:~/Desktop$ gpg –armor –export-secret-subkeys [email protected] > subkeys.key
ubuntu@ubuntu:~/Desktop$ gpg –armor –export [email protected] > public.key
Public Key is OK to save it in your “online” computer or cloud drives, you will have to use it to encrypt your files or emails.
Install “scdaemon” for Smart Card operations
This step is to temporarily connect Ubuntu live USB to the internet and install “scdaemon” for Smart Card operations, once done disconnect your internet immediately.
Make sure the needed repositories are selected
Install “scdaemon”
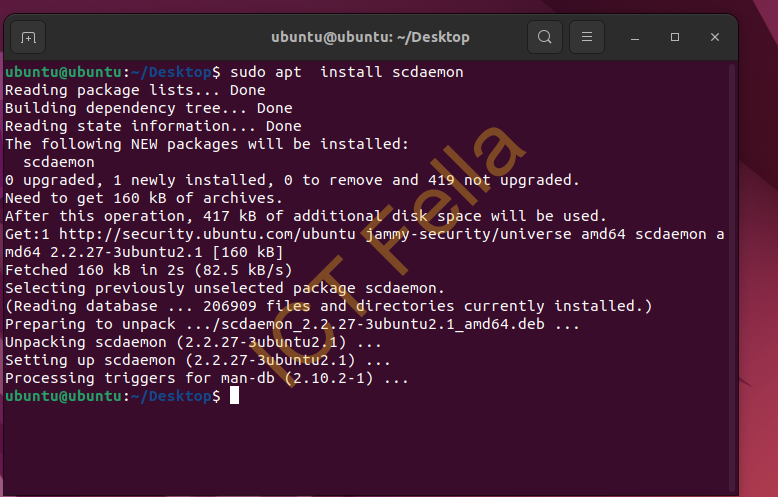
Disconnect your internet imediately after installation.
Change Yubikey PIN and Yubikey Admin PIN
Now connect your Yubikey and change the password.
ubuntu@ubuntu:~/Desktop$ gpg --edit-card
Reader ...........: 1050:04cccccccccccdf:0
Application ID ...: D2ccccccccc00
Application type .: OpenPGP
Version ..........: 3.4
Manufacturer .....: Yubico
Serial number ....: 2057xxxxx
Name of cardholder: [not set]
Language prefs ...: [not set]
Salutation .......:
URL of public key : [not set]
Login data .......: [not set]
Signature PIN ....: not forced
Key attributes ...: rsa2048 rsa2048 rsa2048
Max. PIN lengths .: 127 127 127
PIN retry counter : 3 0 3
Signature counter : 0
KDF setting ......: off
Signature key ....: [none]
Encryption key....: [none]
Authentication key: [none]
General key info..: [none]
gpg/card> admin (go to admin mode)
Admin commands are allowed
gpg/card> passwd
gpg: OpenPGP card no. D2xxxxxxxxxxxxxxxxxxxxxxxx000 detected
1 - change PIN
2 - unblock PIN
3 - change Admin PIN
4 - set the Reset Code
Q - quit
Your selection? 1
Error changing the PIN: Bad PIN
1 - change PIN
2 - unblock PIN
3 - change Admin PIN
4 - set the Reset Code
Q - quit
Your selection? 1 (the default PIN is 123456)
PIN changed.
1 - change PIN
2 - unblock PIN
3 - change Admin PIN
4 - set the Reset Code
Q - quit
Your selection? 3 (the default admin PIN is 12345678)
PIN changed.
1 - change PIN
2 - unblock PIN
3 - change Admin PIN
4 - set the Reset Code
Q - quit
Your selection? q
gpg/card> quitMove the Primay Key into Yubikey
ubuntu@ubuntu:~/Desktop$ gpg --edit-key [email protected]
gpg (GnuPG) 2.2.27; Copyright (C) 2021 Free Software Foundation, Inc.
This is free software: you are free to change and redistribute it.
There is NO WARRANTY, to the extent permitted by law.
Secret key is available.
sec rsa4096/3xxxxxxxxxxxxxxxxx6
created: 2023-03-12 expires: 2033-03-09 usage: SC
trust: ultimate validity: ultimate
ssb rsa4096/FxxxxxxxxxxxxxxxxxxC2
created: 2023-03-12 expires: 2033-03-09 usage: E
ssb rsa4096/6xxxxxxxxxxxxxxxxA30
created: 2023-03-12 expires: 2033-03-09 usage: A
[ultimate] (1). yubikey1 (yubikey1) <[email protected]>
gpg> keytocard
Really move the primary key? (y/N) y
Please select where to store the key:
(1) Signature key
(3) Authentication key
Your selection? 1
sec rsa4096/3xxxxxxxxxxxxxxxxxxx6
created: 2023-03-12 expires: 2033-03-09 usage: SC
trust: ultimate validity: ultimate
ssb rsa4096/FxxxxxxxxxxxxxxxxxxxxC2
created: 2023-03-12 expires: 2033-03-09 usage: E
ssb rsa4096/6Cxxxxxxxxxxxxxx0
created: 2023-03-12 expires: 2033-03-09 usage: A
[ultimate] (1). yubikey1 (yubikey1) <[email protected]>
Move the Encryption Key into Yubikey
ubuntu@ubuntu:~/Desktop$ gpg --edit-key [email protected]
gpg (GnuPG) 2.2.27; Copyright (C) 2021 Free Software Foundation, Inc.
This is free software: you are free to change and redistribute it.
There is NO WARRANTY, to the extent permitted by law.
Secret key is available.
sec rsa4096/3xxxxxxxxxxxxxxxxxxxxxxx6
created: 2023-03-12 expires: 2033-03-09 usage: SC
trust: ultimate validity: ultimate
ssb rsa4096/Fxxxxxxxxxxxxxxxxxxxxx2
created: 2023-03-12 expires: 2033-03-09 usage: E
ssb rsa4096/6xxxxxxxxxxxxxxxxxxxxxxxxx30
created: 2023-03-12 expires: 2033-03-09 usage: A
[ultimate] (1). yubikey1 (yubikey1) <[email protected]>
gpg> key 1
sec rsa4xxxxxxxxxxxxxxxxxxxxxxxxxxxxxxx36
created: 2023-03-12 expires: 2033-03-09 usage: SC
trust: ultimate validity: ultimate
ssb* rsa4096/FBxxxxxxxxxxxxxxxxxxxxxx2 (please check the * make sure the correct key is selected)
created: 2023-03-12 expires: 2033-03-09 usage: E
ssb rsa4096/6xxxxxxxxxxxxxxxxxxxxxx30
created: 2023-03-12 expires: 2033-03-09 usage: A
[ultimate] (1). yubikey1 (yubikey1) <[email protected]>
gpg> keytocard
Please select where to store the key:
(2) Encryption key
Your selection? 2
sec rsa4096/3xxxxxxxxxxxxxxxxxxxxxxxxx36
created: 2023-03-12 expires: 2033-03-09 usage: SC
trust: ultimate validity: ultimate
ssb* rsa4096/FBExxxxxxxxxxxxxxxxxxxxxxxxxx2
created: 2023-03-12 expires: 2033-03-09 usage: E
ssb rsa4096/6C8xxxxxxxxxxxxxx0
created: 2023-03-12 expires: 2033-03-09 usage: A
[ultimate] (1). yubikey1 (yubikey1) <[email protected]>
Move the Authentication key into Yubikey
ubuntu@ubuntu:~/Desktop$ gpg --edit-key [email protected]
gpg (GnuPG) 2.2.27; Copyright (C) 2021 Free Software Foundation, Inc.
This is free software: you are free to change and redistribute it.
There is NO WARRANTY, to the extent permitted by law.
Secret key is available.
sec rsa4096/3xxxxxxxxxxxxxxxxxxxxxxxxx6
created: 2023-03-12 expires: 2033-03-09 usage: SC
trust: unknown validity: unknown
ssb rsa4096/FBxxxxxxxxxxxxxxxxxxC2
created: 2023-03-12 expires: 2033-03-09 usage: E
ssb rsa4096/6Cxxxxxxxxxxxxxxxxxx0
created: 2023-03-12 expires: 2033-03-09 usage: A
[ unknown] (1). yubikey1 (yubikey1) <[email protected]>
gpg> key 2
sec rsa4096/3xxxxxxxxxxxxxxxxxxxxxxxxxxxxxxx6
created: 2023-03-12 expires: 2033-03-09 usage: SC
trust: unknown validity: unknown
ssb rsa4096/xxxxxxxxxxxxxxxxxxxxxxxxxxxx2
created: 2023-03-12 expires: 2033-03-09 usage: E
ssb* rsa4096/6xxxxxxxxxxxxxxxxxxxxxxxxxxx0 (please check the * make sure the correct key is selected)
created: 2023-03-12 expires: 2033-03-09 usage: A
[ unknown] (1). yubikey1 (yubikey1) <[email protected]>
gpg> keytocard
Please select where to store the key:
(3) Authentication key
Your selection? 3
sec rsa4096/3Fxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxx6
created: 2023-03-12 expires: 2033-03-09 usage: SC
trust: unknown validity: unknown
ssb rsa4096/FxxxxxxxxxxxxxxxxxxxxxxxxxC2
created: 2023-03-12 expires: 2033-03-09 usage: E
ssb* rsa4096/6Cxxxxxxxxxxxxxxxxxxxxxxx0
created: 2023-03-12 expires: 2033-03-09 usage: A
[ unknown] (1). yubikey1 (yubikey1) <[email protected]>
gpg> quit
Save changes? (y/N) y (Remember to save the change here)You can repeat the previous 3 steps for your backup Yubikey
Useful links
Using Your YubiKey with OpenPGP – Yubico
