Issue Assessment
Windows 10 Client with Domain User/Computer certificate
Window Server 2022 with NPS role installed, network policy configured with “Smart Card or Certificate” authentication (802.1x)
2 tiers Root CA setup: 1x Offline Root CA and 1x Subordinate Root CA
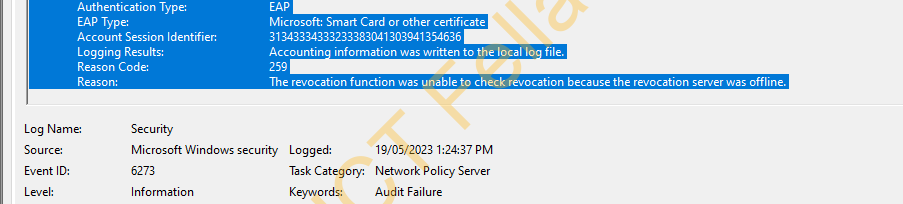
Windows 10 Client error “Cannot connect to this network”, Event Viewer log as below
Reason: Explicit Eap failure received
Error: 0x40420110
EAP Reason: 0x40420110NPS Server Auditing is enabled
auditpol /set /subcategory:”Network Policy Server” /success:enable /failure:enableNPS Server log
"The revocation function was unable to check revocation because the revocation server was offline"
Reason code: 259
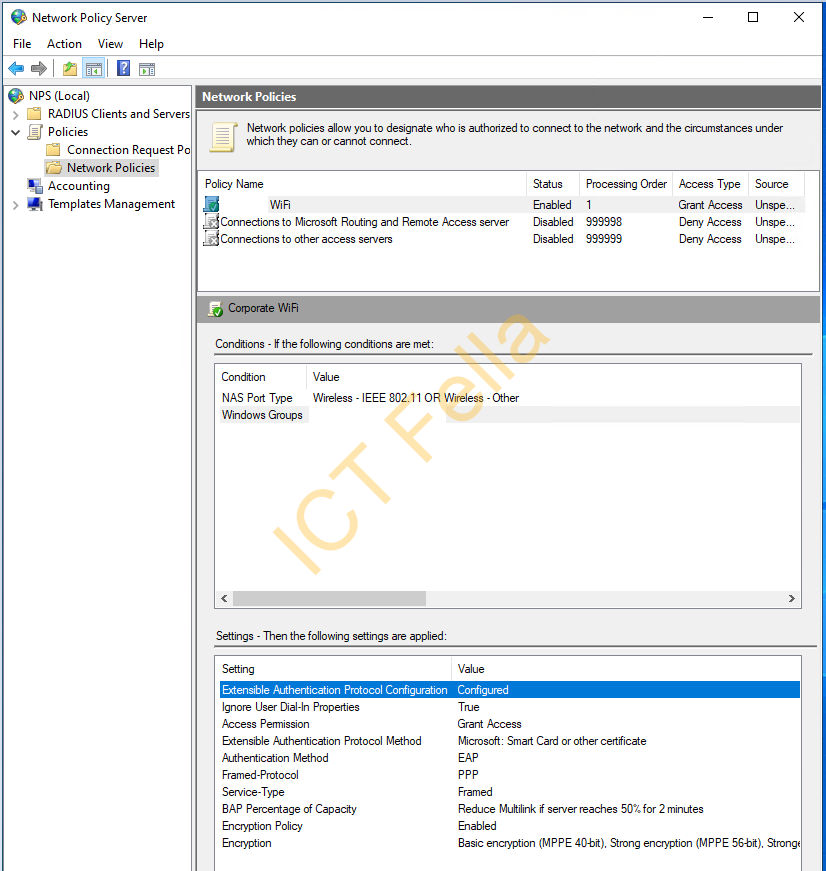
Check NPS configuration and Server Certificate
NPS network policy is ok
Constraints is configured with correct certificate
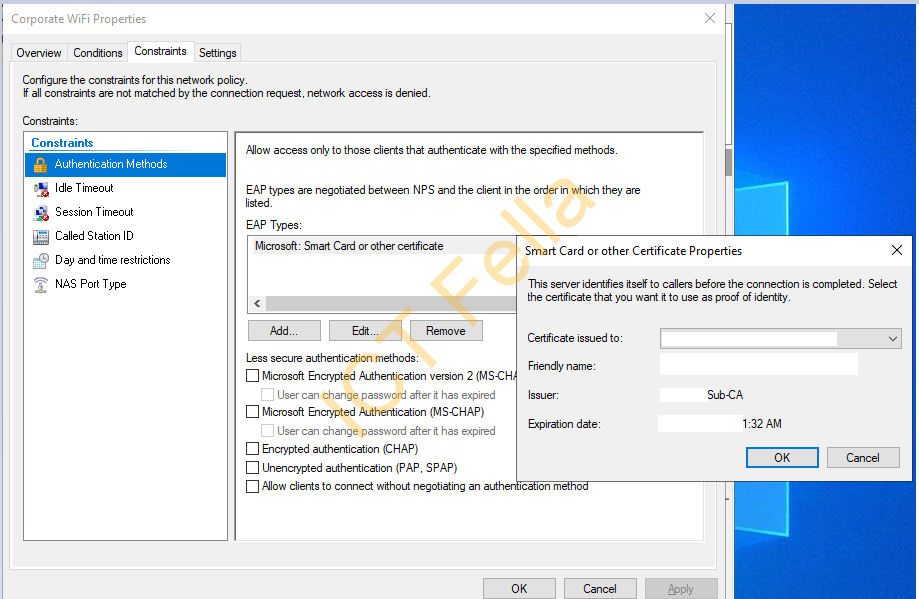
NPS Server Certificate is good
1. Subject is NOT empty
2. Enhanced Key Usage: Server Authentication and Client Authentication
3. Key Usage: Digital Signature, Key Encipherment (a0)
Check PKI Root CA configuration
PKIview is NOT good
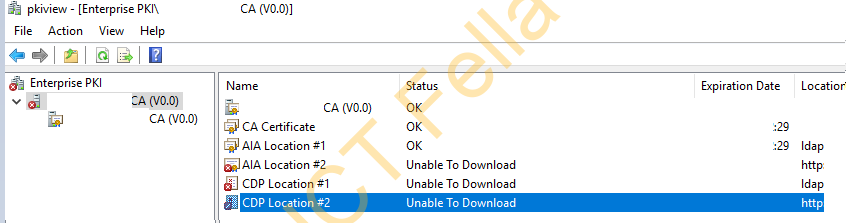
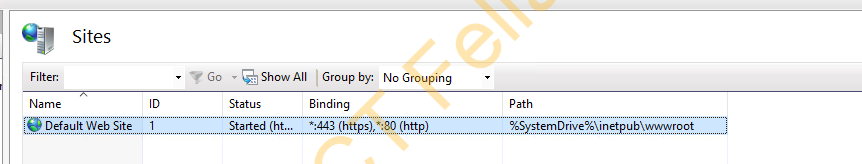
How to Fix
In my case, to fix the “AIA Location#2 and CDP Location #2”, I have to configure the IIS binding on the published CRL server to accept port 80, as my CRL is configured with HTTP but HTTP binding is NOT Configured on CRL IIS service
“CDP Location #1” LDAP path is confiugred with the wrong ADEI configuration path by using the wrong server name “RootCA“
certutil -f -dspublish "C:\temp\OfflineRootCA.crl" RootCAPublish the CRL using the correct server name in the environment:
certutil -f -dspublish "C:\temp\OfflineRootCA.crl" ICTFellaCA02