Object
IPtables is probably one of the most useful tools widely integrated into the majority of the Linux Distributions, this article is to share the iptables used on my VPS in the past 7-8 years. I have hosted my personal Asterisk PBX in the VPS so I can make international calls via Twilio SIP Trunk. I will share the Asterisk config in a separate post.
Environment
- A OpenVZ Virutal Private Server hosted in HostUS, with Centos Minimal installed, It is kind of old but still waiting for Rocky Linux to save the world 🙂
[test@admin ~]# lsb_release -d
Virtualization: openvz
Operating System: CentOS Linux 7 (Core)
CPE OS Name: cpe:/o:centos:centos:7
Kernel: Linux 3.10.0
Architecture: x86-642. iptables 1.4.21
3. A simple line is added into /etc/rc.local file, so the IPtables script can be started automatically when the VPS boots up.
IPtables Content
#setup default explicit policies to block
/sbin/iptables -F
/sbin/iptables -P INPUT DROP
/sbin/iptables -P OUTPUT DROP
/sbin/iptables -P FORWARD DROP
#Allow any traffic over the loopback interface
/sbin/iptables -A INPUT -i lo -j ACCEPT
/sbin/iptables -A OUTPUT -o lo -j ACCEPT
#Deny any incoming packets that claiming to be yourself and funny loopback packets
/sbin/iptables -A INPUT -i eth0 -s 127.0.0.1 -j LOG
/sbin/iptables -A INPUT -i eth0 -s 127.0.0.1 -j DROP
#Deny any funny “internal” and “multicast” packets
/sbin/iptables -A INPUT -s 192.168.0.0/16 -j LOG
/sbin/iptables -A INPUT -s 172.16.0.0/16 -j LOG
/sbin/iptables -A INPUT -s 224.0.0.0/4 -j LOG
/sbin/iptables -A INPUT -s 240.0.0.0/5 -j LOG
/sbin/iptables -A INPUT -s 192.168.0.0/16 -j DROP
/sbin/iptables -A INPUT -s 172.16.0.0/16 -j DROP
/sbin/iptables -A INPUT -s 224.0.0.0/4 -j DROP
/sbin/iptables -A INPUT -s 240.0.0.0/5 -j DROP
#Masquerading rules, it was used for my OpenVPN package, 10.8.0.0/23 is the “SSL-VPN Subnet”
echo “1” > /proc/sys/net/ipv4/ip_forward
/sbin/iptables -A FORWARD -m state –state RELATED,ESTABLISHED -j ACCEPT
/sbin/iptables -A INPUT -s 10.8.0.0/23 -j ACCEPT
/sbin/iptables -A FORWARD -s 10.8.0.0/23 -j ACCEPT
/sbin/iptables -A FORWARD -j REJECT
/sbin/iptables -t nat -A POSTROUTING -s 10.8.0.0/23 -j MASQUERADE
/sbin/iptables -A INPUT -m state –state ESTABLISHED,RELATED -j ACCEPT
/sbin/iptables -A OUTPUT -m state –state NEW,ESTABLISHED,RELATED -j ACCEPT
#Allow ICMP packets except for redirect packets(tpye 5)
/sbin/iptables -A INPUT -p icmp –icmp-type 5 -j DROP
/sbin/iptables -A INPUT -p icmp -j ACCEPT
/sbin/iptables -A OUTPUT -p icmp -j ACCEPT
/sbin/iptables -A FORWARD -p icmp -j ACCEPT
#use input chain to control source ip address
/sbin/iptables -A INPUT -s 49.0.0.0/8 -j ACCEPT
/sbin/iptables -A INPUT -p tcp –dport 443 -j ACCEPT
/sbin/iptables -A INPUT -p tcp –dport 13943:13948 -j ACCEPT
/sbin/iptables -A INPUT -p tcp –dport 10000:10100 -j ACCEPT
/sbin/iptables -A INPUT -p tcp –dport 14945 -j ACCEPT/sbin/iptables -A INPUT -p tcp –dport 443 -j ACCEPT
/sbin/iptables -A INPUT -p udp –dport 443 -j ACCEPT
/sbin/iptables -A INPUT -p tcp –dport 4443 -j ACCEPT
/sbin/iptables -A INPUT -p udp –dport 4443 -j ACCEPT
#drop unused ports
/sbin/iptables -A INPUT -p tcp –dport 80 -j ACCEPT
#email rules: only use outcoming email for alert, not for incoming emails
/sbin/iptables -A FORWARD -p tcp –dport 25 -j ACCEPT
/sbin/iptables -A FORWARD -p tcp –dport 143 -j ACCEPT
/sbin/iptables -A INPUT -p tcp –dport 25 -j DROP
/sbin/iptables -A INPUT -p tcp –dport 143 -j DROP
#asterisk rules, block the comon SIP attack first, then allow registration ONLY via DNS, drop all other registrations via IP address, drop SIP Options, and other throttling rules for SIP traffic. Note: This section can drop 99% of the SIP attacks!
/sbin/iptables -A INPUT -m string –string “sundayddr” –algo kmp –icase -j DROP
/sbin/iptables -A INPUT -m string –string “sipsak” –algo kmp –icase -j DROP
/sbin/iptables -A INPUT -m string –string “sipvicious” –algo kmp –icase –icase -j DROP
/sbin/iptables -A INPUT -m string –string “friendly-scanner” –algo kmp –icase -j DROP
/sbin/iptables -A INPUT -m string –string “iWar” –algo kmp –icase -j DROP
/sbin/iptables -A INPUT -m string –string “sip-scan” –algo kmp –icase -j DROP
/sbin/iptables -A INPUT -m string –string “sipcli” –algo kmp –icase -j DROP
/sbin/iptables -A INPUT -m string –string “eyeBeam” –algo kmp –icase -j DROP
/sbin/iptables -A INPUT -m string –string “VaxSIPUserAgent” –algo kmp –icase -j DROP
/sbin/iptables -A INPUT -m string –string “sip:nm@nm” –algo kmp –icase -j DROP
/sbin/iptables -A INPUT -m string –string “sip:[email protected]” –algo kmp –icase -j DROP\
#
/sbin/iptables -A INPUT -p udp –dport 5060 -m state –state ESTABLISHED,RELATED -j ACCEPT
/sbin/iptables -A INPUT -p udp –dport 5060 -m string –string “REGISTER sip:testtest.sip” –algo kmp –icase -j ACCEPT
/sbin/iptables -A INPUT -p udp –dport 5060 -m string –string “REGISTER sip:” –algo kmp –icase -j DROP
/sbin/iptables -A INPUT -p udp –dport 5060 -m string –string “OPTIONS sip:” –algo kmp –icase -j DROP
/sbin/iptables -A INPUT -p udp –dport 5060 -m string –string “sip:442030930112” –algo kmp –icase -j DROP
/sbin/iptables -A INPUT -p udp –dport 5060 -m string –string “REGISTER sip:” –algo kmp –icase -m recent –update –seconds 60 –hitcount 12 –rttl –name SIP_1 -j DROP
/sbin/iptables -A INPUT -p udp –dport 5060 -m string –string “INVITE sip:” –algo kmp –icase –to 65535 -m recent –set –name SIP_2
/sbin/iptables -A INPUT -p udp –dport 5060 -m string –string “INVITE sip:” –algo kmp –icase –to 65535 -m recent –update –seconds 60 –hitcount 12 –rttl –name SIP_2 -j DROP
/sbin/iptables -A INPUT -p udp –dport 5060 -m string –string “INVITE sip:” –algo kmp –icase -j ACCEPT
/sbin/iptables -A INPUT -p udp -m hashlimit –hashlimit 6/sec –hashlimit-mode srcip,dstport –hashlimit-name tunnel_limit -m udp –dport 5060 -j ACCEPT
/sbin/iptables -A INPUT -p udp –dport 5060 -j DROP
/sbin/iptables -A INPUT -p udp –dport 10000:20000 -j ACCEPT
Useful Command
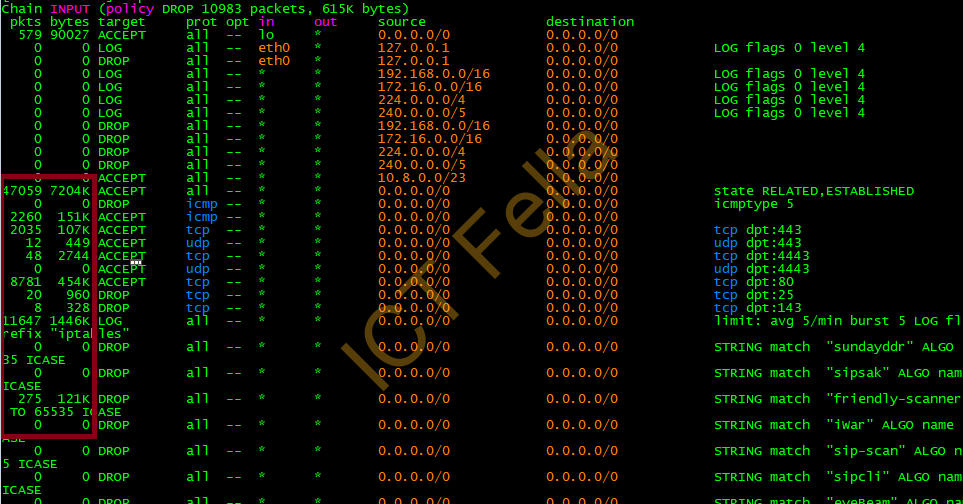
List out the effective IPtables rules and traffic hits
iptables -L -nv
Useful Links
https://wiki.centos.org/HowTos/Network/IPTables
https://wiki.archlinux.org/title/iptables
