This post is about configuring IPsec VPN between Cisco FTD/FMC Firepower and Fortinet FortiGate firewall
Environment
Cisco FTD firewall on routed mode and managed by FMC
Fortinet FortiGate Firewall
Note: Feel free to modify the Phase1 and Phase2 settings based on your security requirements
Fortinet FortiGate Firewall Configuration
Go to “VPN – IPsec Tunnels – Create New – IPsec Tunnel”, give it a name and select “Custom”
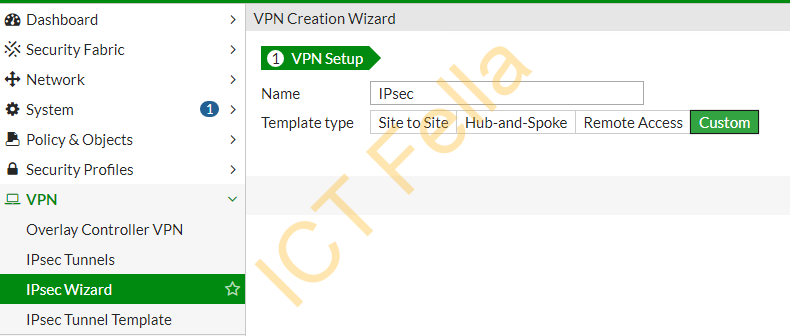
Configure the VPN Tunnels as below
Network
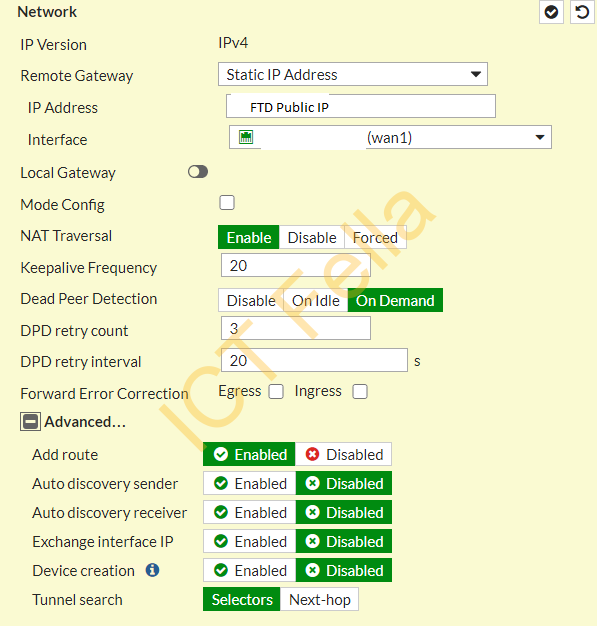
Authentication /IKE
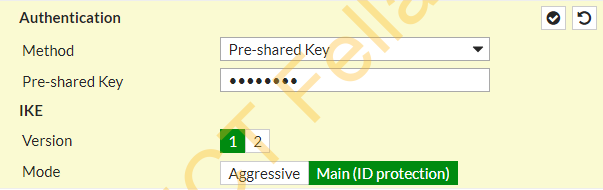
Phase1 Proposal
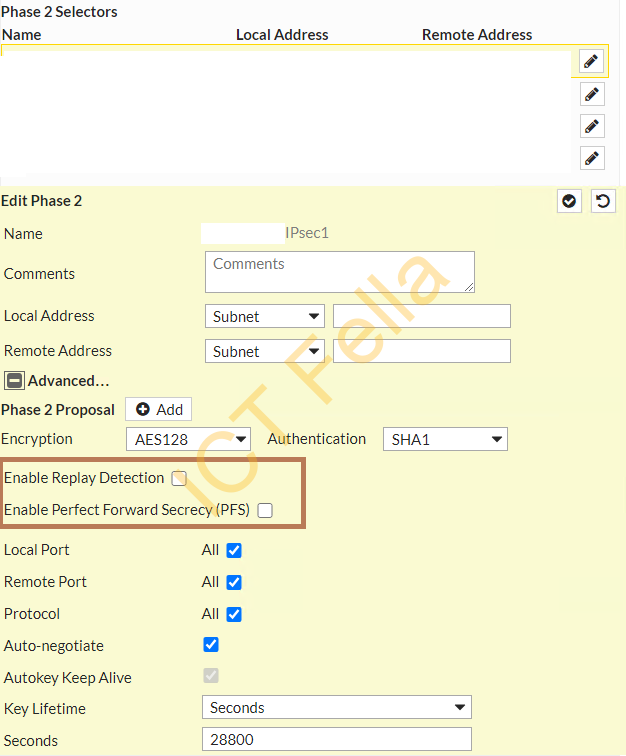
Phase2 Selectors
Please make sure “Relay Detection” and “PFS” are DISABLED
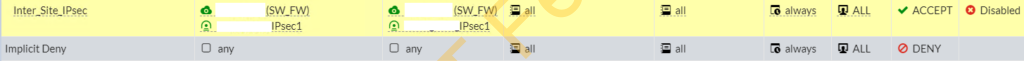
Add new security policies to allow inter-site traffic
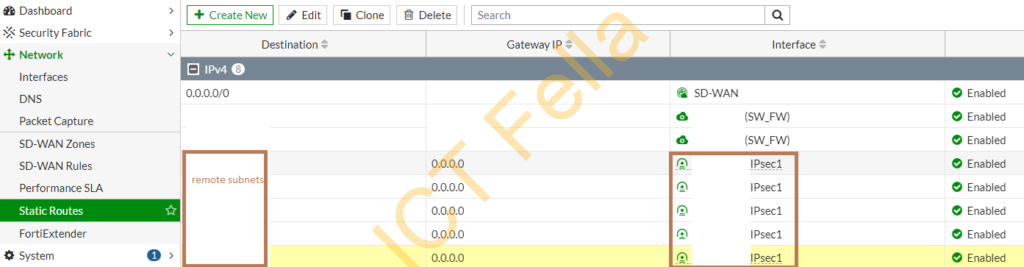
Add new routes so the firewall knows how to route the traffic
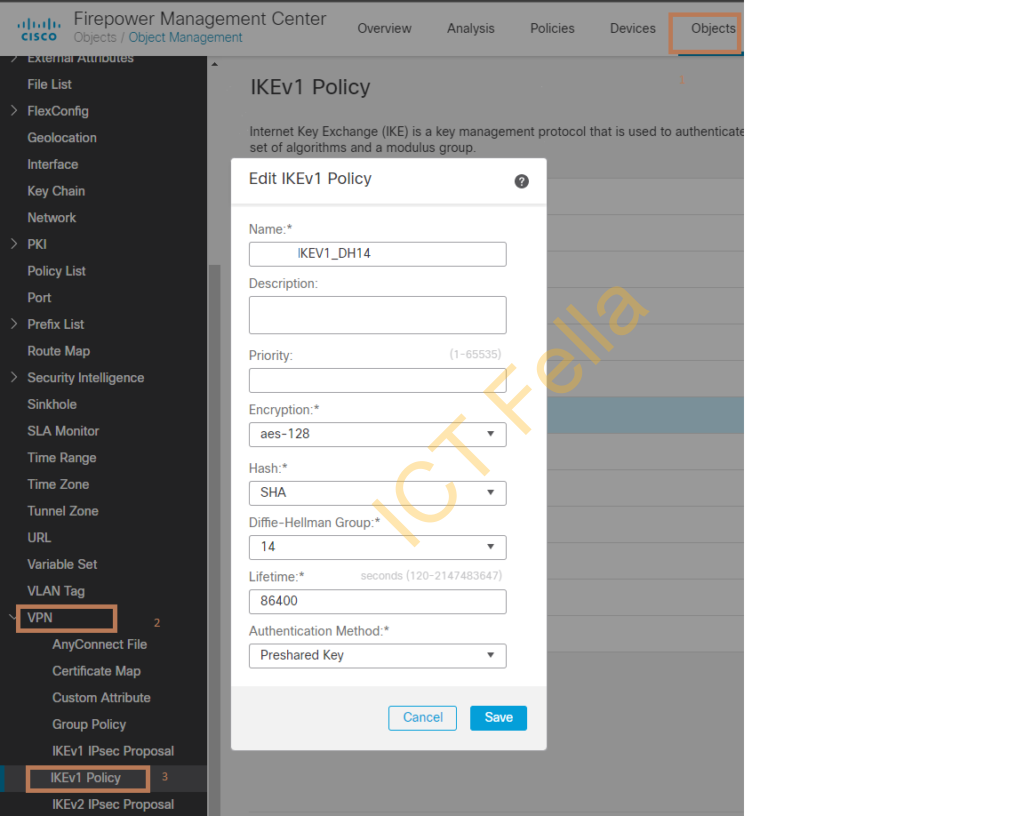
Cisco FMC/FTD Configuration
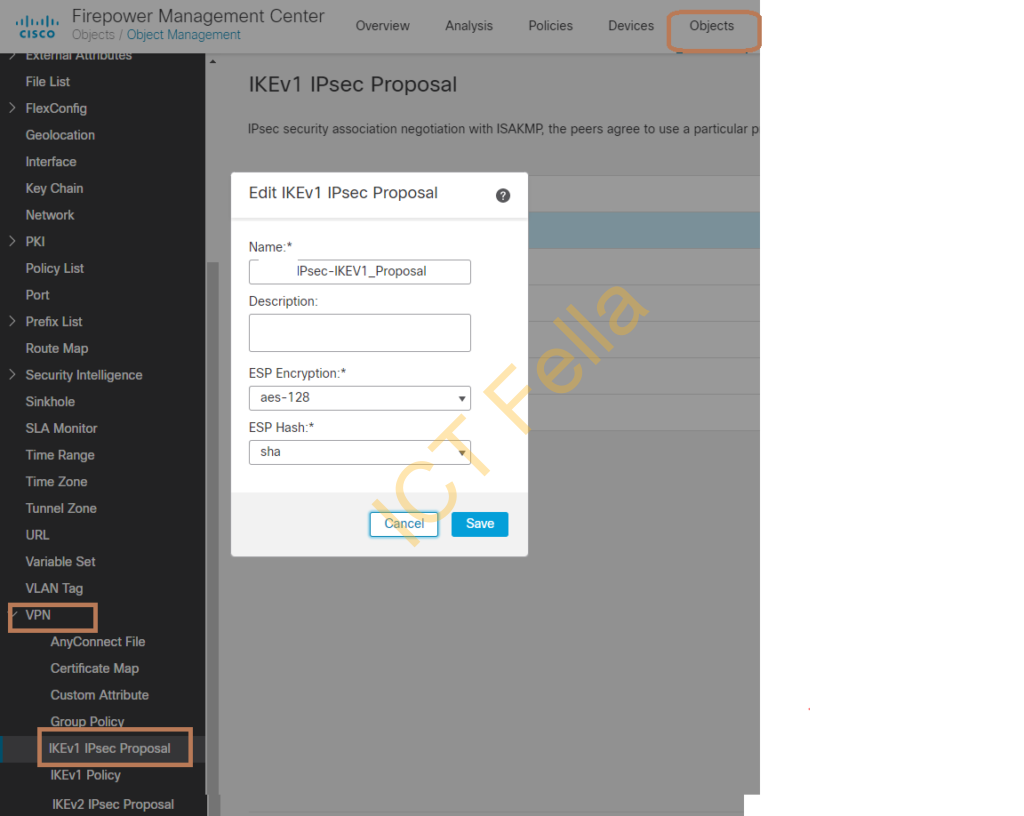
log into Cisco FMC, go to “Objects – VPN – IKEv1 Policy” and configure the same encryption/hash/DH group as what you did in FortiGate firewall
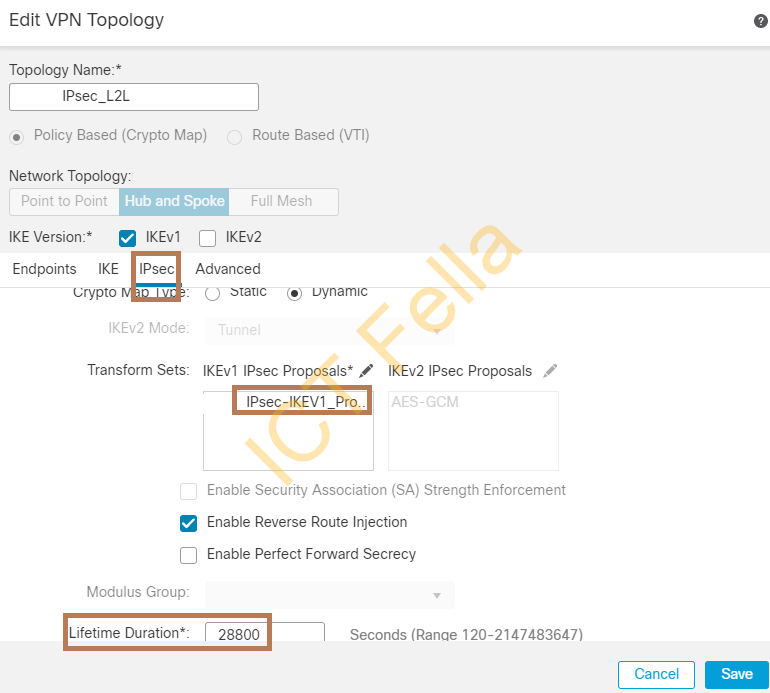
Configure the Phase 2 IPsec policy
Go to ” Devices – Site to Site” and add your VPN
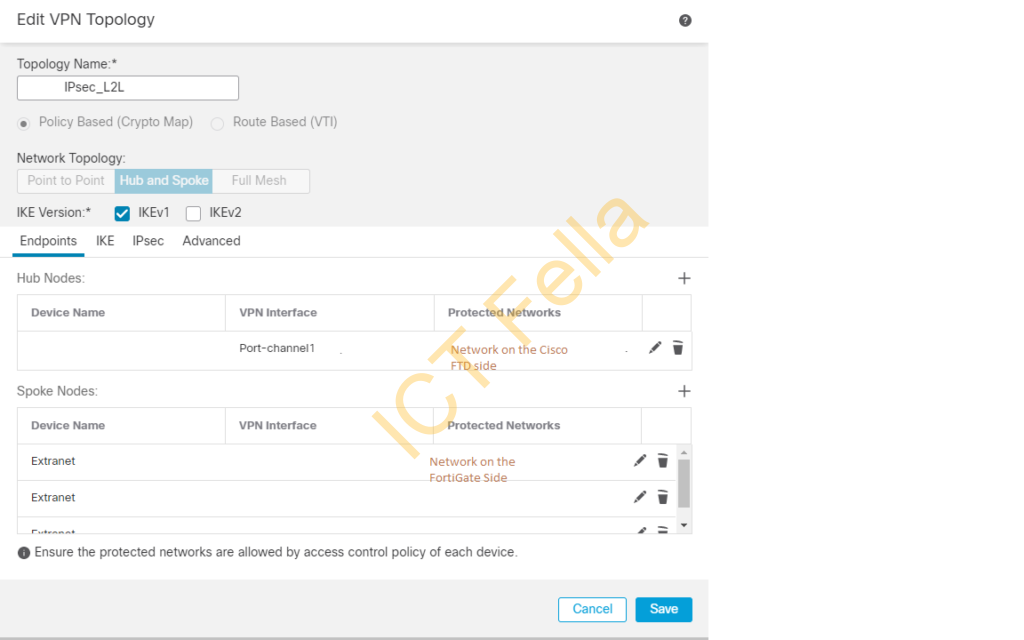
In this example, I am adding a “spoke” location under this “Policy Based (Crypto Map) topology
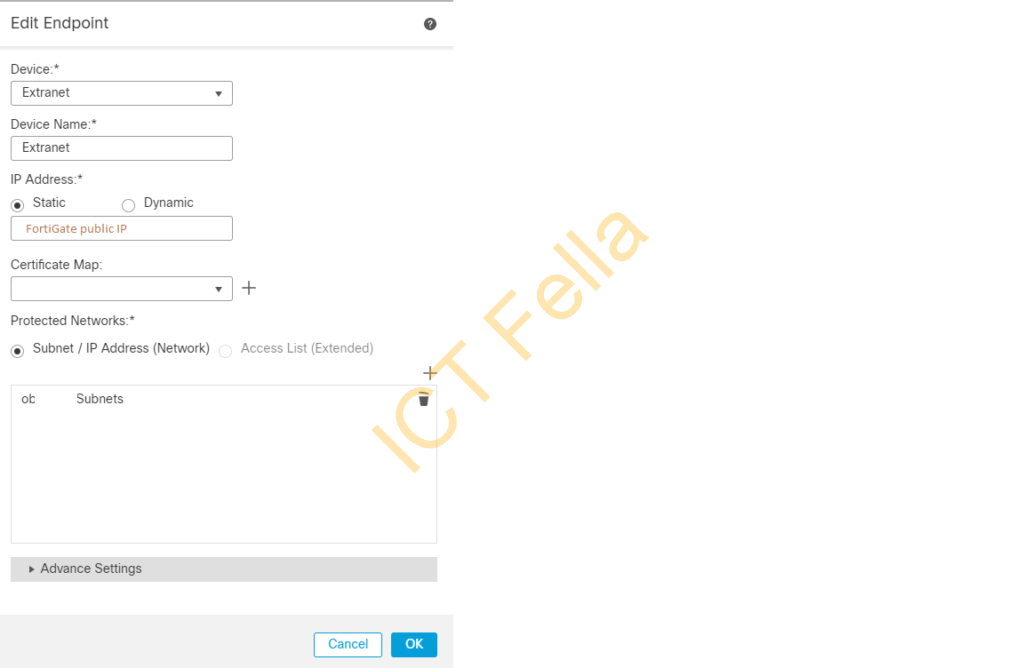
Add new spoke nodes and add FortiGate public IP and remote network object(s)
Make sure the pre-configure IKEv1 policy is selected under IKE Phase1 configuration
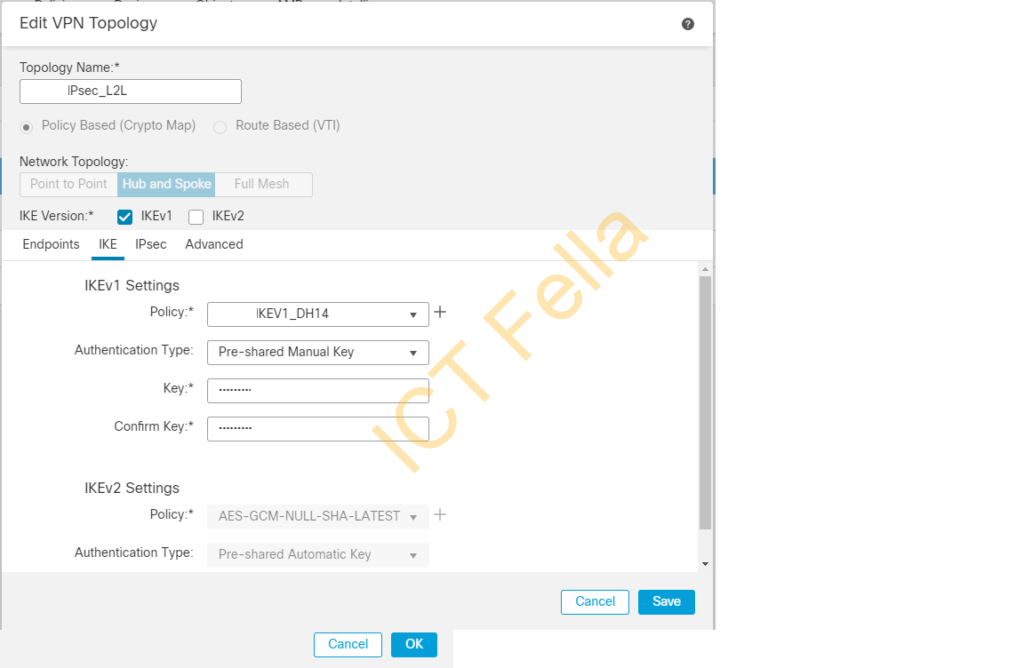
Make sure IPsec Phase2 policy is selected and lifetime etc is the same as on FortiGate Firewall
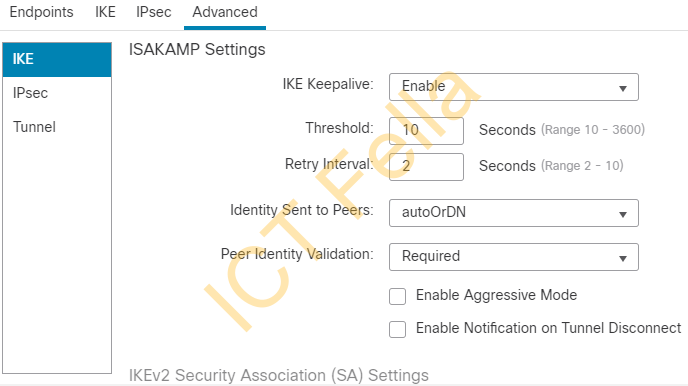
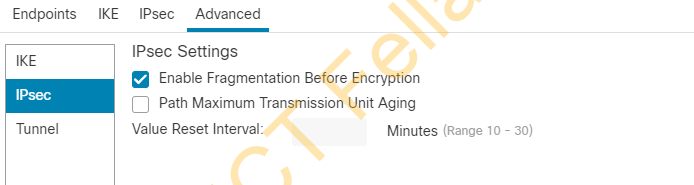
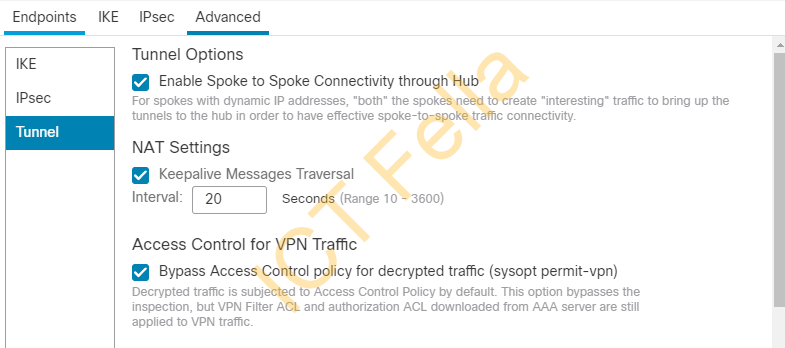
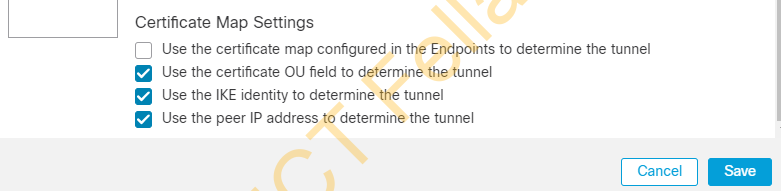
Advanced setting under VPN Topology
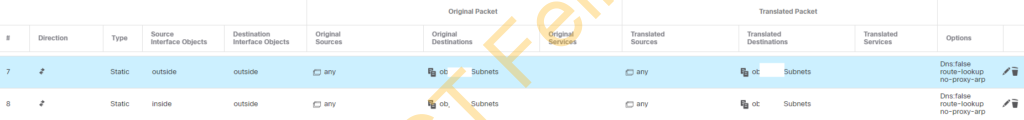
Add needed “NO-NAT” rules so anything inter-site traffic towards FortiGate Remote network is NOT “NATed”
Troubleshooting
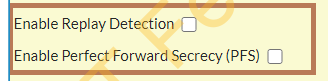
IPsec tunnel does not turn up and Fortinet has error “IPsec phase 1 error” or “no proposal chosen”, when you try to bring up the IPsec on from Fortinet GUI, only phase 1 is green. In my case the issue is PFS and “Relay Detection” and “PFS” are enabled.
Turn both features off to fix the issue
Useful link
