This post is to document the process of configuring dynamic IPsec VPN from Juniper SRX to FortiGate Firewall, then configure OSPF over IPsec tunnel interfaces with a bit of OSPF route filtering.
Environment
1 x Fortinet FortiGate Firewall with dynamic WAN IP address
1 x Juniper SRX firewall with Static WAN IP address
Requirement is to configure Dynamic IPsec VPN (dial out VPN) and running OSPF over the IPsec VPN tunnel interfaces for the inter-site traffic
FortiGate FW dial up to Juniper SRX with defined local ID (Aggressive Mode)
Juniper SRX Configuration
====Configure Phase 1 proposal and policy====
set security ike proposal ike-phase1-proposal authentication-method pre-shared-keys
set security ike proposal ike-phase1-proposal dh-group group2
set security ike proposal ike-phase1-proposal authentication-algorithm sha1
set security ike proposal ike-phase1-proposal encryption-algorithm aes-128-cbc
set security ike policy ike-policy-ICTFella mode aggressive
set security ike policy ike-policy-ICTFella proposals ike-phase1-proposal
set security ike policy ike-policy-ICTFella pre-shared-key ascii-text "ictfella.com"====Configure Phase1 Gateway Configuration and refer to the Phase1 Proposal and Policy====
set security ike gateway ike-FORTI-JUNIP-via-ISP1 ike-policy ike-policy-ICTFella
set security ike gateway ike-FORTI-JUNIP-via-ISP1 dynamic hostname ICTFellaFORTIFW01 (accepting connection from Fortinet)
set security ike gateway ike-FORTI-JUNIP-via-ISP1 dead-peer-detection always-send
set security ike gateway ike-FORTI-JUNIP-via-ISP1 dead-peer-detection interval 10
set security ike gateway ike-FORTI-JUNIP-via-ISP1 dead-peer-detection threshold 3
set security ike gateway ike-FORTI-JUNIP-via-ISP1 external-interface reth1.22 (WAN port)====Configure Phase 2 proposal and policy-======
set security ipsec proposal ipsec-phase2-proposal authentication-algorithm hmac-sha1-96
set security ipsec proposal ipsec-phase2-proposal encryption-algorithm aes-128-cbc
set security ipsec policy ipsec-policy-ICTFella proposals ipsec-phase2-proposal======Configure Phase2 IPsec====
set security ipsec vpn ipsec-FORTI-JUNIP-via-ISP1 bind-interface st0.24
set security ipsec vpn ipsec-FORTI-JUNIP-via-ISP1 ike gateway ike-FORTI-JUNIP-via-ISP1
set security ipsec vpn ipsec-FORTI-JUNIP-via-ISP1 ike ipsec-policy ipsec-policy-ICTFella
set security ipsec vpn ipsec-FORTI-JUNIP-via-ISP1 establish-tunnels immediately====set and add the tunnel interface into the new Security zone====
set interfaces st0 unit 24 family inet address 10.0.0.49/29
set security zones security-zone FORTI interfaces st0.24 host-inbound-traffic system-services ping
set security zones security-zone FORTI interfaces st0.24 host-inbound-traffic protocols ospf====allow inter-site traffic====
set security policies from-zone FORTI to-zone JUNIP_Inside policy permit-JUNIP_Inside match source-address any
set security policies from-zone FORTI to-zone JUNIP_Inside policy permit-JUNIP_Inside match destination-address any
set security policies from-zone FORTI to-zone JUNIP_Inside policy permit-JUNIP_Inside match application any
set security policies from-zone FORTI to-zone JUNIP_Inside policy permit-JUNIP_Inside then permit
set security policies from-zone JUNIP_Inside to-zone FORTI policy permit-JUNIP_Inside2 match source-address any
set security policies from-zone JUNIP_Inside to-zone FORTI policy permit-JUNIP_Inside2 match destination-address any
set security policies from-zone JUNIP_Inside to-zone FORTI policy permit-JUNIP_Inside2 match application any
set security policies from-zone JUNIP_Inside to-zone FORTI policy permit-JUNIP_Inside2 then permit===Enable OSPF and Enable the route-map filtering for OSPF advertisement===
set routing-options static route 0.0.0.0/0 next-hop x.x.x.x
set routing-options static route 172.16.0.0/24 next-hop 10.0.0.14
set routing-options router-id 10.0.0.1
set protocols ospf export into-ospf
set protocols ospf area 0.0.0.0 interface st0.24 metric 150
set policy-options policy-statement into-ospf term 10 from protocol direct
set policy-options policy-statement into-ospf term 10 then accept
set policy-options policy-statement into-ospf term 20 from protocol static
set policy-options policy-statement into-ospf term 20 from route-filter 0.0.0.0/0 exact
set policy-options policy-statement into-ospf term 20 then reject
set policy-options policy-statement into-ospf term 30 from protocol static
set policy-options policy-statement into-ospf term 30 then acceptFortinet FortiGate Configuration
====Remote Gateway====
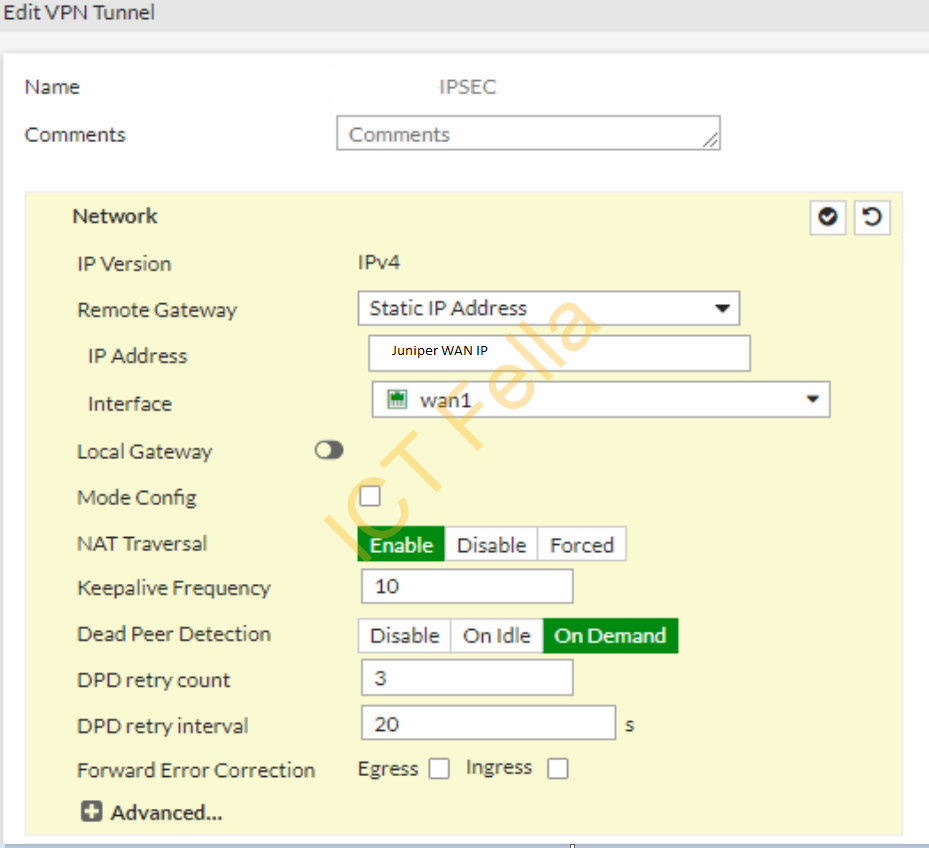
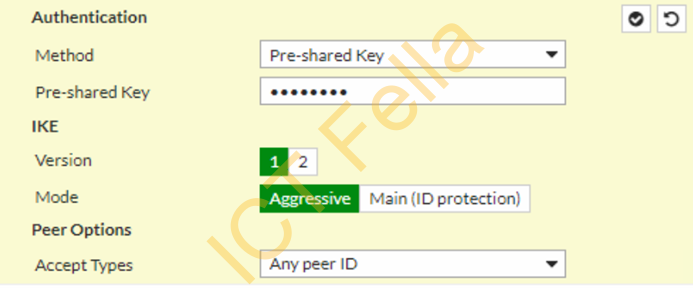
====Authentication and IKE Configure: Aggressive mode – Accept Any Peer ID=====
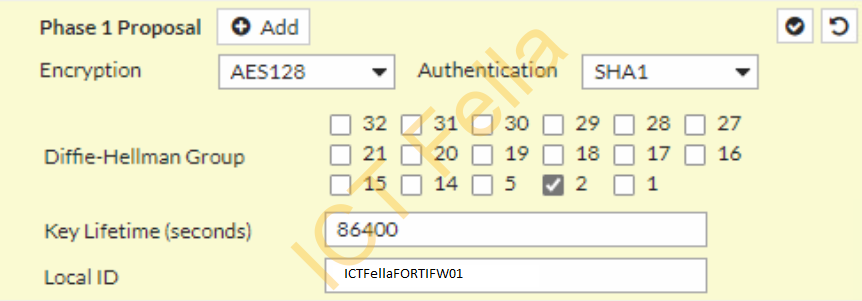
==== Phase1 Proposal and define the local ID====
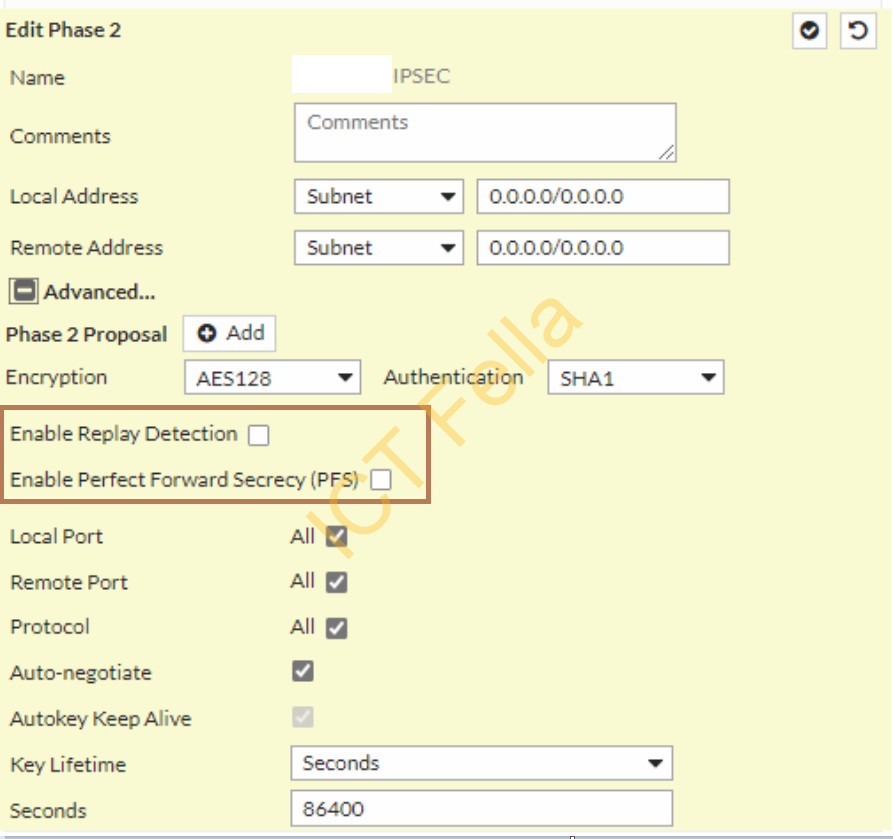
====Phase 2 Config====
====Allow inter-site Traffic====

====Config Tunnel Interface====
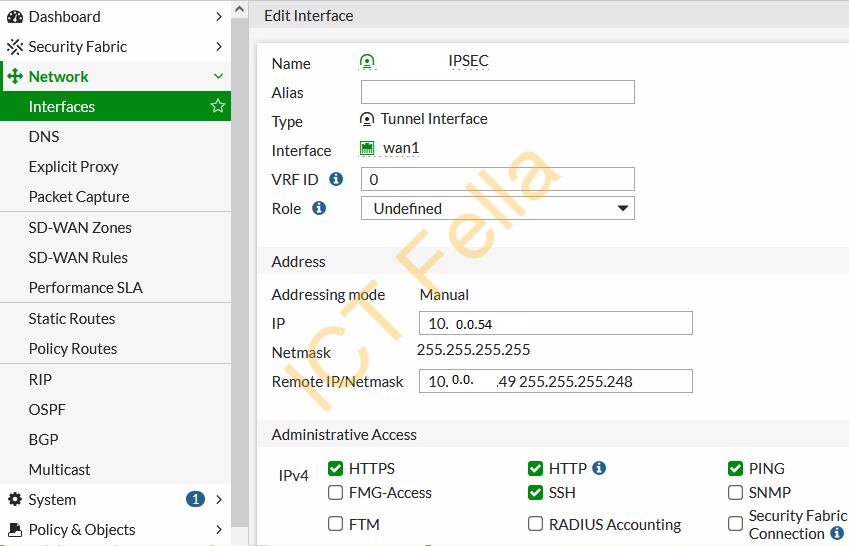
====Configure OSPF====
config router ospf
set router-id 10.1.1.1
config area
edit 0.0.0.0
next
end
config ospf-interface
edit "IPsec"
set interface "IPSEC"
set cost 150
set mtu-ignore enable (without this ospf will stuck at Exchange state)
set network-type point-to-point
next
end
config network
edit 1
set prefix 10.0.0.0 255.255.255.0
next
end
config redistribute "connected"
end
config redistribute "static"
set status enable
set routemap "RM_Static_to_OSPF"
end
config redistribute "rip"
end
config redistribute "bgp"
end
config redistribute "isis"
end
end
====Route-map config to limit the routes out====
config router route-map
edit "RM_Static_to_OSPF"
config rule
edit 1
set match-ip-address "AL_Static_to_OSPF"
unset set-ip-nexthop
unset set-ip6-nexthop
unset set-ip6-nexthop-local
unset set-originator-id
next
end
next
end
====Configure ACL to limit the route=====
config router access-list
edit "AL_Static_to_OSPF"
config rule
edit 1
set prefix 10.1.2.0 255.255.0.0
set exact-match enable
next
end
next
end
