This post is to document the process to configure static IPsec VPN between Fortinet and Sophos Firewall.
Environment
- 1x Fortinet Fortigate Firewall cluster running at active-passive mode
- 1x Sophos UTM Firewall
- Both sides have static public IP assigned
- Phase 1 and Phase 2 use the same encryption (AES256) and authentication (SHA256) algorithm, Group 14 or Group 5 are selected for the Diffie-hellman process.
Configure Fortigate firewall
Go to “VPN” – “IPsec Wizard”, start the new VPN wizard, give it a sensible name and choose “Custom” as the template type
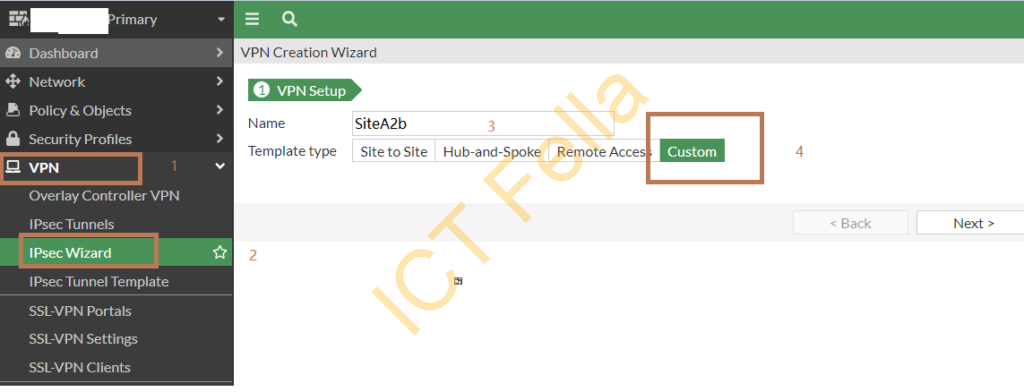
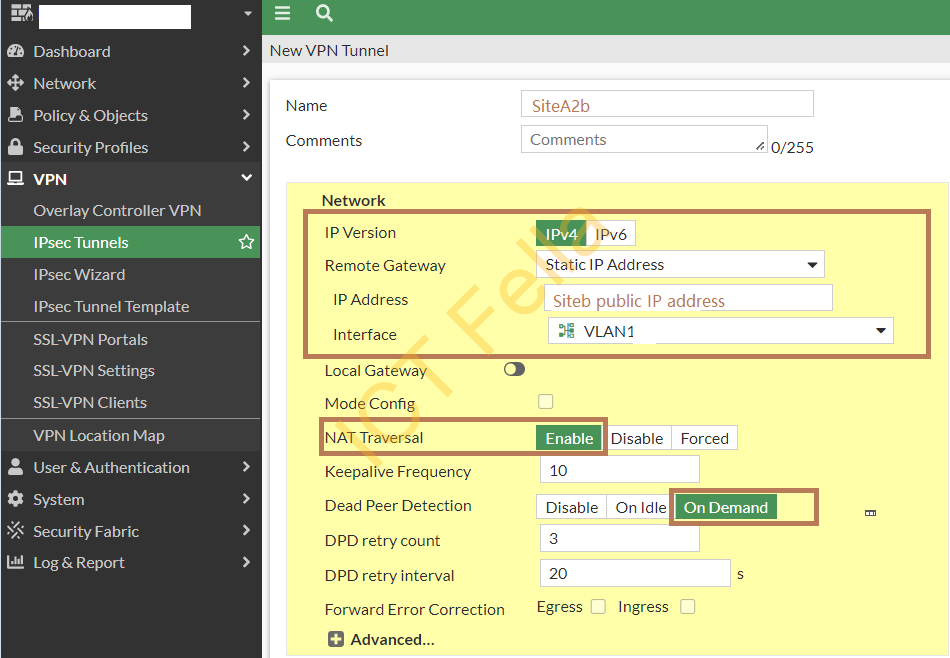
Give it a name, choose “static IP address” in Remote Gateway, put Site b public IP address in and choose your “WAN” port as the source interface
In the Authentication and Phase1 Proposal section, we have chosen
1. Pre-Shared Key
2. IKE V1
3. Main (ID protection) mode
4. AES256 for Encryption and SHA256 for Authentication
5. Diffie-Hellman Groups 14 and 5
6. Key lifetime: 86400 seconds
7. XAuth: disabled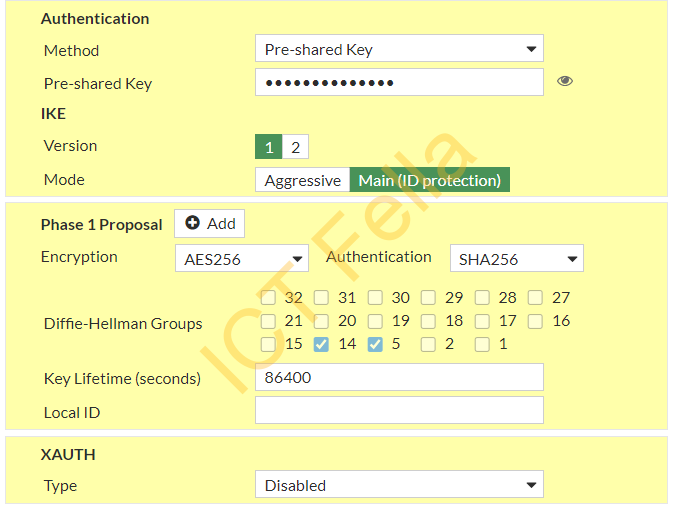
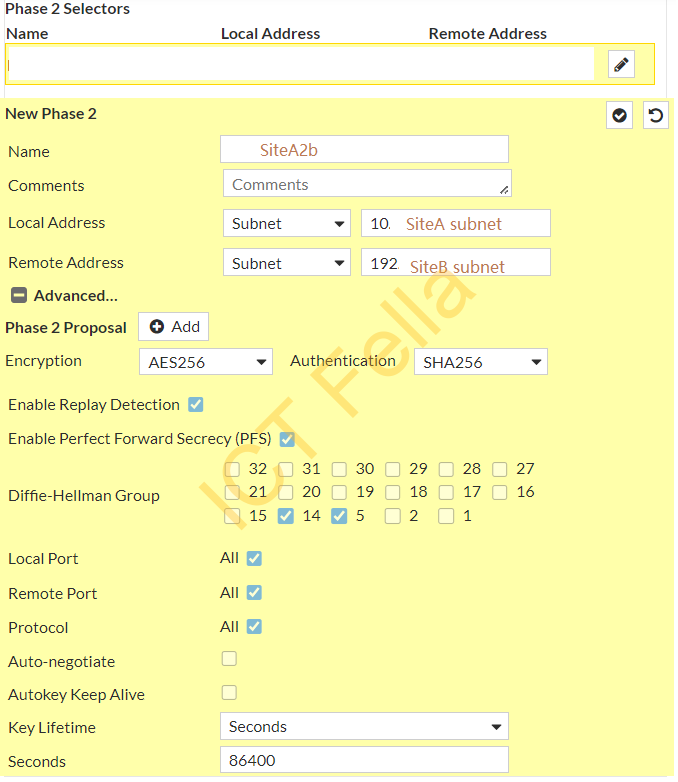
In Phase 2 Selectors, we have defined the local and remote subnets, the same encryption and authentication for the phase2 proposal:
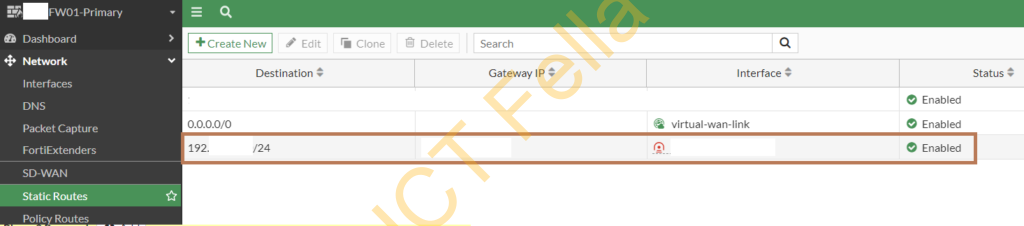
Add a new route to go to Site B subnet:
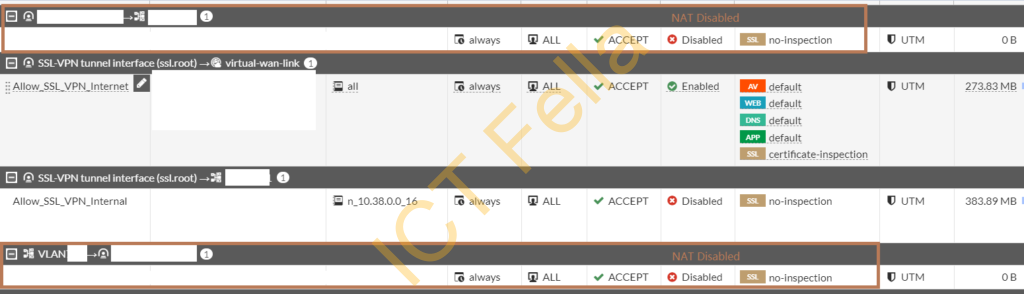
Add needed policy on both ways to allow the inter-site traffic, please make sure NAT is disabled for inter-site traffic
Sophos UTM Firewall
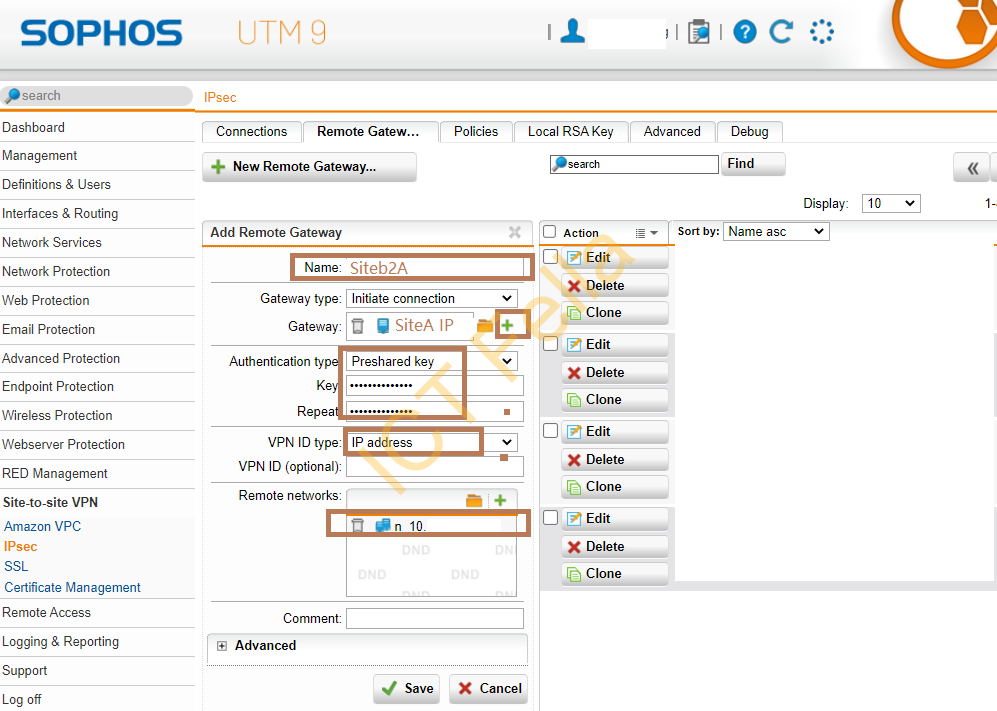
In the “Remote Gateway” tab, add a new remote gateway to march up the Fortigate firewall configuration
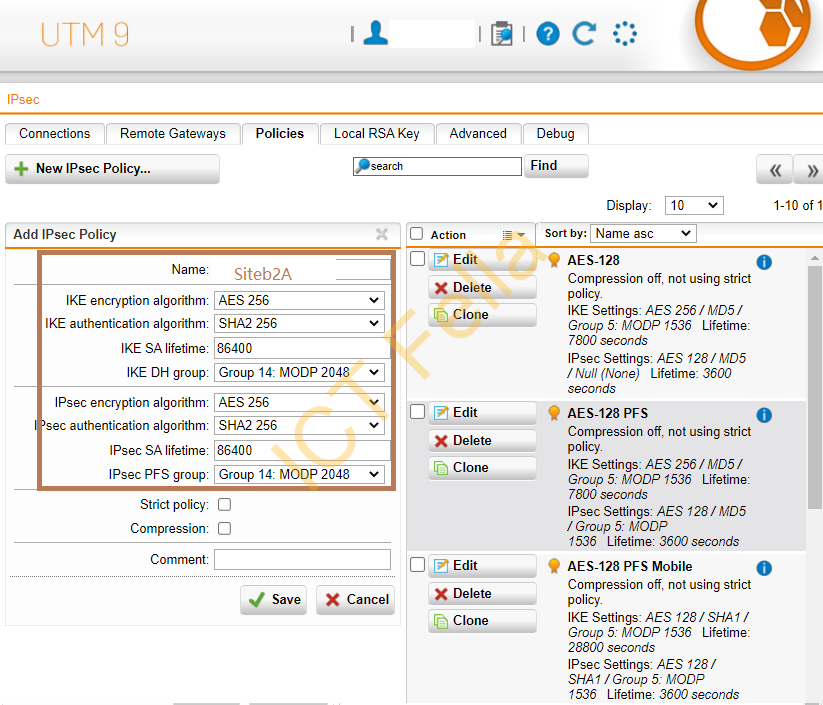
In the “Policies” tab, add a new IPsec Policy to match up the Fortigate firewall configuration
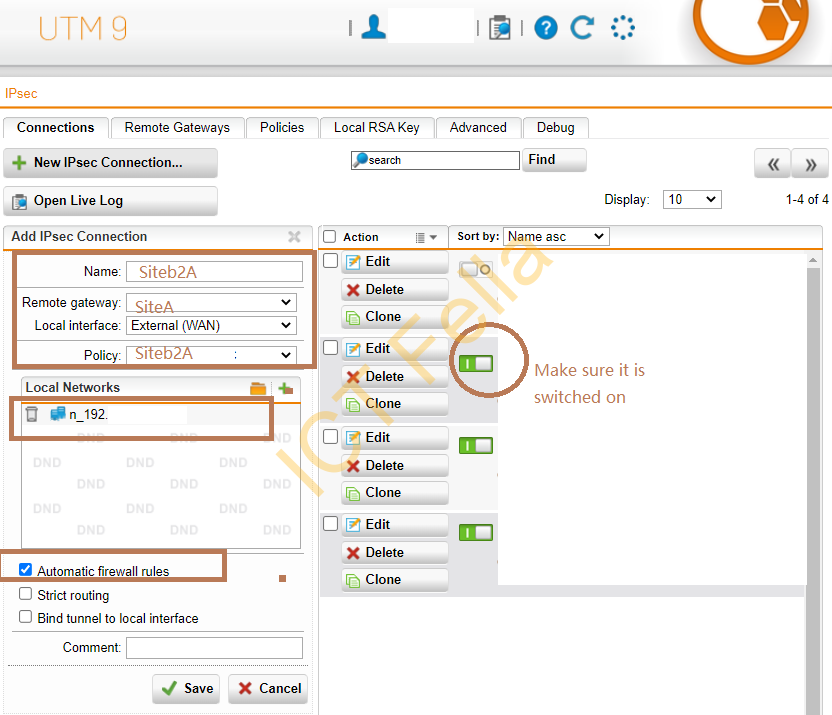
In the “Connection” tab, link the remote gateways and policies together, make sure the new IPsec connection is switched on.
Bring up the IPsec interface in the Fortigate firewall
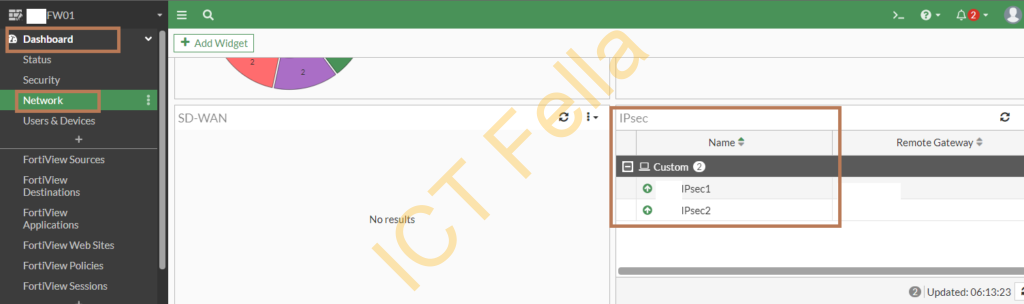
Go to the “Dashboard” – “Network” -“IPsec” widget, you can see your IPsec interface status
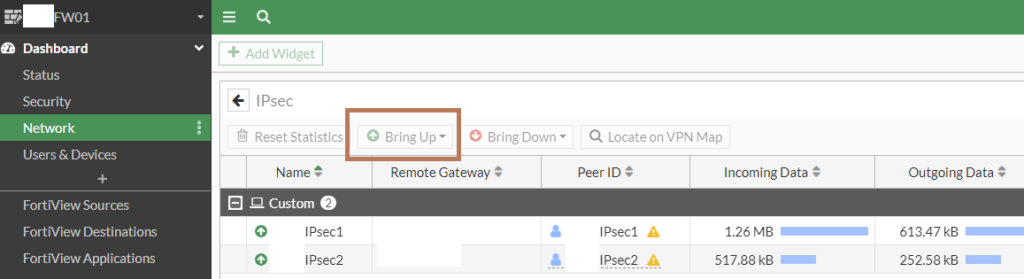
If you want to manually bring up the IPsec interface, click into the widget and bring it up
Useful links
https://docs.fortinet.com/document/fortigate/6.0.0/handbook/791718/ipsec-vpn-from-the-gui
