Eve-NG is the most used network emulation software for network professionals. Similar to Webiou or Unetlab in the older days, you can create virtual network devices for the majority of the IT networking vendors in a simple web GUI. This post is to demonstrate how to simulate or configure the Internet in the EVE-NG lab environment.
Environment
- Eve-NG 2.0.3-112 community edition hosted in ESXi host 7.0
root@eve-ng:/opt/unetlab/addons/qemu/fortinet-FGT-v6-build1914# dpkg -l eve-ng
Desired=Unknown/Install/Remove/Purge/Hold
| Status=Not/Inst/Conf-files/Unpacked/halF-conf/Half-inst/trig-aWait/Trig-pend
|/ Err?=(none)/Reinst-required (Status,Err: uppercase=bad)
||/ Name Version Architecture Description
+++-===========================-==================-==================-============================================================
ii eve-ng 2.0.3-112 amd64 A new generation software for networking labs.- Eve-NG is deployed via .ova file and has access to the internet- “Bridged” via ESXi host, you can treat this VM NIC the same as a normal Windows VM when you are configuring it.
- A DHCP server is configured for the same port group/VLAN/Subnet of the EVE-NG VM, in my case, it is my core switch
- The virtual switch configure used has the below security policies turned off
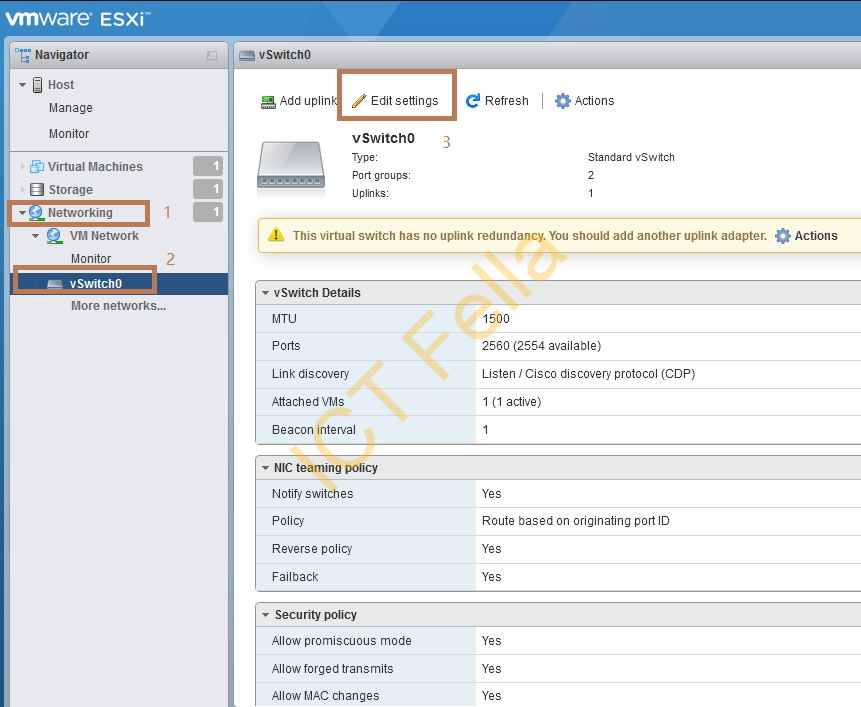
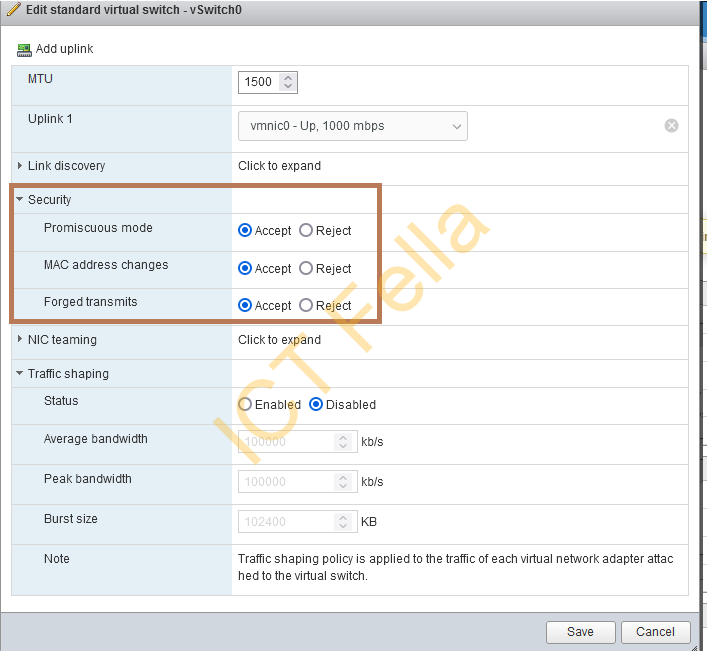
Method 1 – Double NAT via EVE-NG VM NIC
This is the most common and easy way if you want to give your “nested” network device internet access
Assume you have got EVE-NG running, open your lab and right-click in a blank space, select “Network”
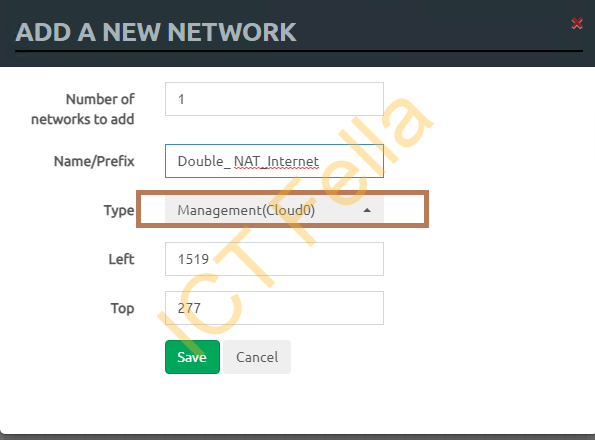
Give it a name and make sure “Management(Clould0) is selected
I have selected a Fortinet Fortigate Firewall in this case
The Port1 of my Firewall’s configuration is on DHCP by default, let’s assume it is my “WAN” port, check the configuration of Fortigate interfaces:
FortiGate-VM64-KVM # show system interface
config system interface
edit "port1"
set vdom "root"
set mode dhcp
set allowaccess ping https ssh fgfm
set type physical
set snmp-index 1
next
edit "port2"
set vdom "root"
set type physical
set snmp-index 2
next
edit "port3"
set vdom "root"
set type physical
set snmp-index 3Check the IP address of each interface of Fortigate firewall via “show system interface ?“, equivalent to “sh ip int brief” in Cisco. Also, check the ping to the real internet
FortiGate-VM64-KVM # show system interface ?
name Name.
fortilink static 0.0.0.0 0.0.0.0 169.254.1.1 255.255.255.0 up disable aggregate enable
port1 dhcp 0.0.0.0 0.0.0.0 10.98.0.199 255.255.255.0 up disable physical enable
port2 static 0.0.0.0 0.0.0.0 0.0.0.0 0.0.0.0 up disable physical enable
port3 static 0.0.0.0 0.0.0.0 0.0.0.0 0.0.0.0 up disable physical enable
port4 static 0.0.0.0 0.0.0.0 0.0.0.0 0.0.0.0 up disable physical enable
ssl.root static 0.0.0.0 0.0.0.0 0.0.0.0 0.0.0.0 up disable tunnel enable
FortiGate-VM64-KVM # execute ping 1.1.1.1
PING 1.1.1.1 (1.1.1.1): 56 data bytes
64 bytes from 1.1.1.1: icmp_seq=0 ttl=56 time=3.1 ms
64 bytes from 1.1.1.1: icmp_seq=1 ttl=56 time=3.6 ms
64 bytes from 1.1.1.1: icmp_seq=2 ttl=56 time=7.6 ms
^C
--- 1.1.1.1 ping statistics ---
3 packets transmitted, 3 packets received, 0% packet loss
round-trip min/avg/max = 3.1/4.7/7.6 ms Method 2 – Configure your own ISPs
In a lot of cases, we would like to test IPsec Site to Site VPN or MPLS links using actual production IPs to save time when handling cutover, the option can be using dynamic routing protocols, for instance, If you are testing OSPF over IPsec or MPLS, you can simulate ISP links using EIGRP, we know it is not in real word 🙂
How to configure the ISP router? Simply advertise your network and you are done
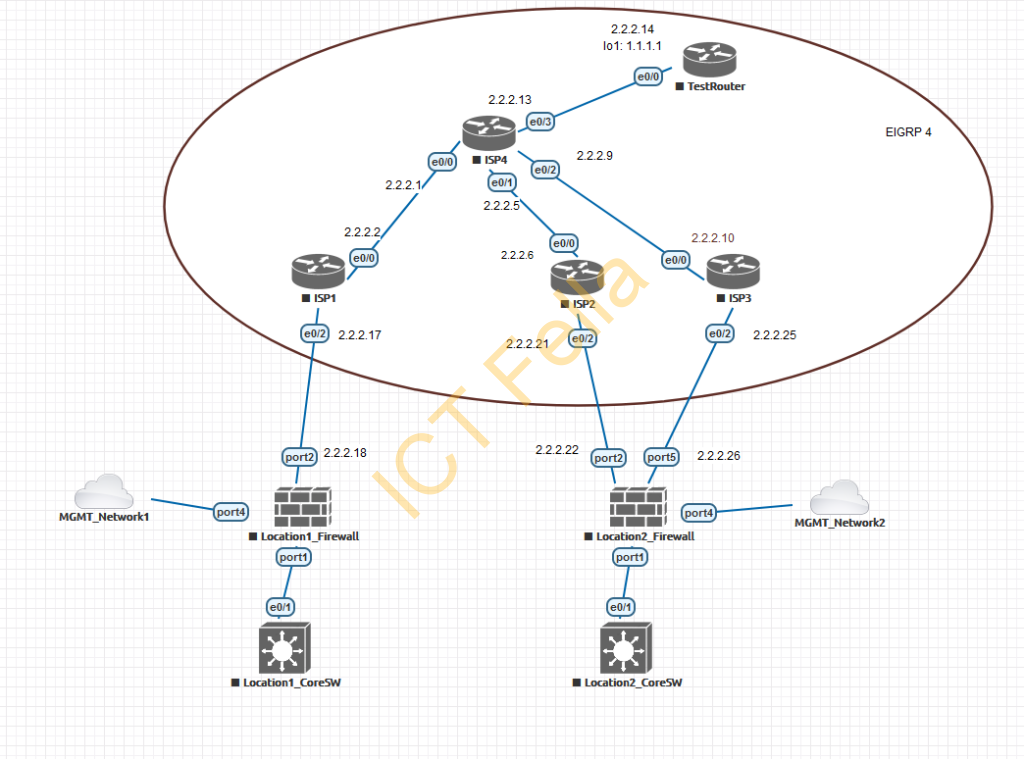
ISP1 Configuration
Conf t
!
hostname ISP1
!
!
interface Ethernet0/0
ip address 2.2.2.2 255.255.255.252
!
interface Ethernet0/1
no ip address
!
interface Ethernet0/2
ip address 2.2.2.17 255.255.255.252
!
interface Ethernet0/3
no ip address
shutdown
!
!
router eigrp 4
network 2.2.2.0 0.0.0.3
network 2.2.2.16 0.0.0.3
!
end
wrISP2 Configuration
conf t
!
hostname ISP2
!
interface Ethernet0/0
ip address 2.2.2.6 255.255.255.252
!
interface Ethernet0/1
no ip address
!
interface Ethernet0/2
ip address 2.2.2.21 255.255.255.252
!
interface Ethernet0/3
no ip address
shutdown
!
!
router eigrp 4
network 2.2.2.4 0.0.0.3
network 2.2.2.20 0.0.0.3
!
end
wrISP3 Configuration
conf t
!
hostname ISP3
!
interface Ethernet0/0
ip address 2.2.2.10 255.255.255.252
!
interface Ethernet0/1
no ip address
!
interface Ethernet0/2
ip address 2.2.2.25 255.255.255.252
!
interface Ethernet0/3
no ip address
shutdown
!
!
router eigrp 4
network 2.2.2.8 0.0.0.3
network 2.2.2.24 0.0.0.3
!
!
end
wrISP4 Configuration
conf t
!
hostname ISP4
!
interface Ethernet0/0
ip address 2.2.2.1 255.255.255.252
!
interface Ethernet0/1
ip address 2.2.2.5 255.255.255.252
!
interface Ethernet0/2
ip address 2.2.2.9 255.255.255.252
!
interface Ethernet0/3
ip address 2.2.2.13 255.255.255.252
!
!
router eigrp 4
network 2.2.2.0 0.0.0.3
network 2.2.2.4 0.0.0.3
network 2.2.2.8 0.0.0.3
network 2.2.2.12 0.0.0.3
!
end
wrTestRouter Configuration
conf t
!
hostname TestRouter
!
interface Loopback1
ip address 1.1.1.1 255.255.255.255
!
interface Ethernet0/0
ip address 2.2.2.14 255.255.255.252
!
interface Ethernet0/1
no ip address
shutdown
!
interface Ethernet0/2
no ip address
shutdown
!
interface Ethernet0/3
no ip address
shutdown
!
!
router eigrp 4
network 1.1.1.1 0.0.0.0
network 2.2.2.12 0.0.0.3
!
end
wr
Verify the connectivity
ISP1>ping 1.1.1.1
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 1.1.1.1, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 1/1/1 ms
ISP1>traceroute 1.1.1.1
Type escape sequence to abort.
Tracing the route to 1.1.1.1
VRF info: (vrf in name/id, vrf out name/id)
1 2.2.2.1 0 msec 0 msec 0 msec
2 2.2.2.14 1 msec 1 msec * Useful Links
https://www.eve-ng.net/images/EVE-COOK-BOOK-1.2.pdf
